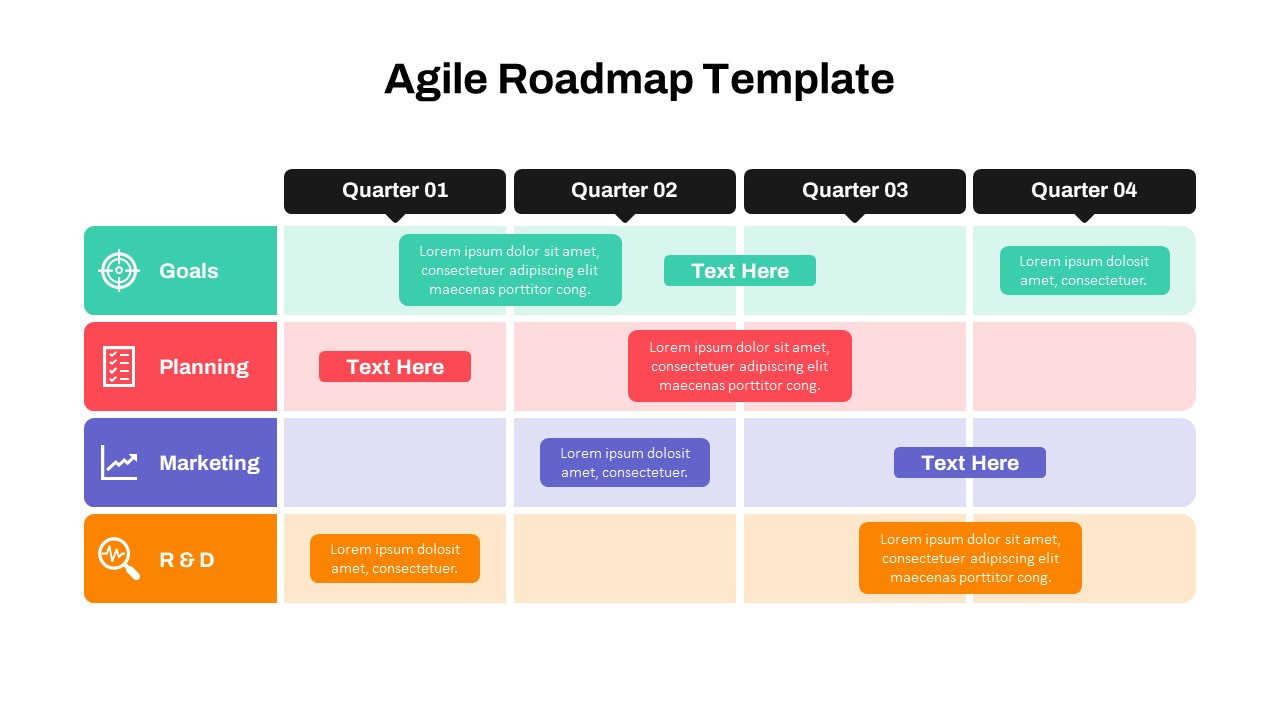
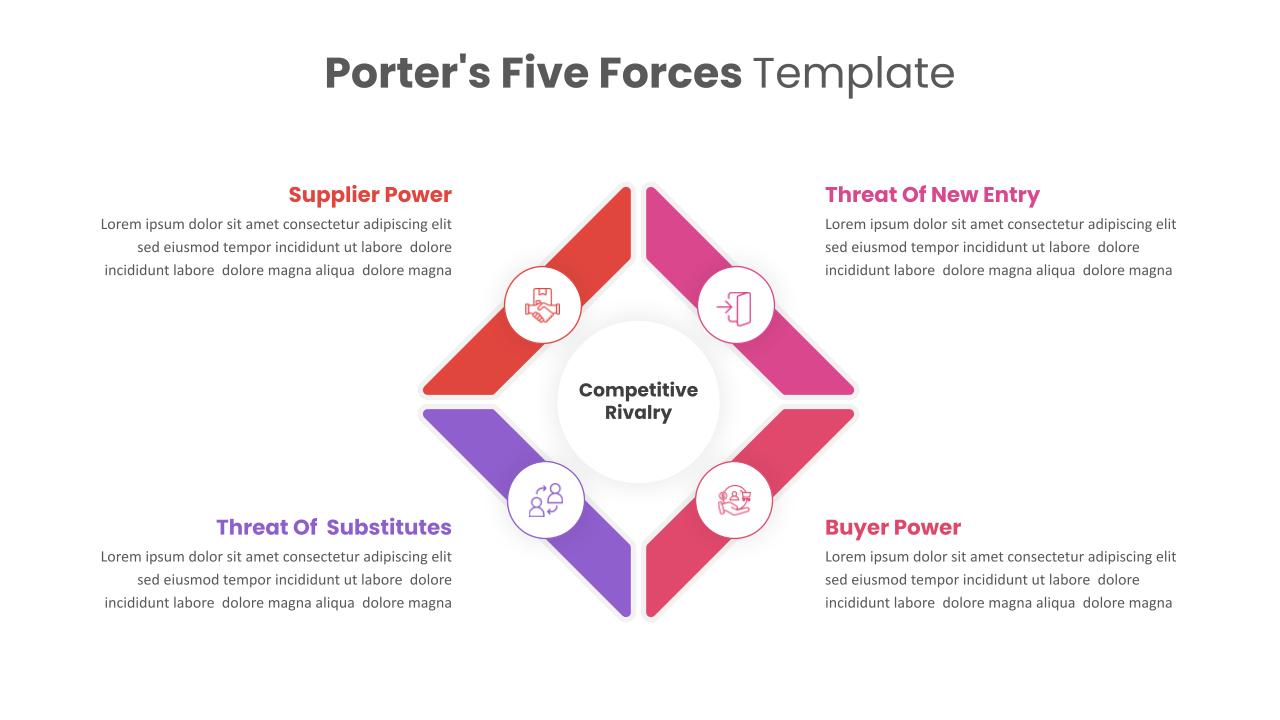
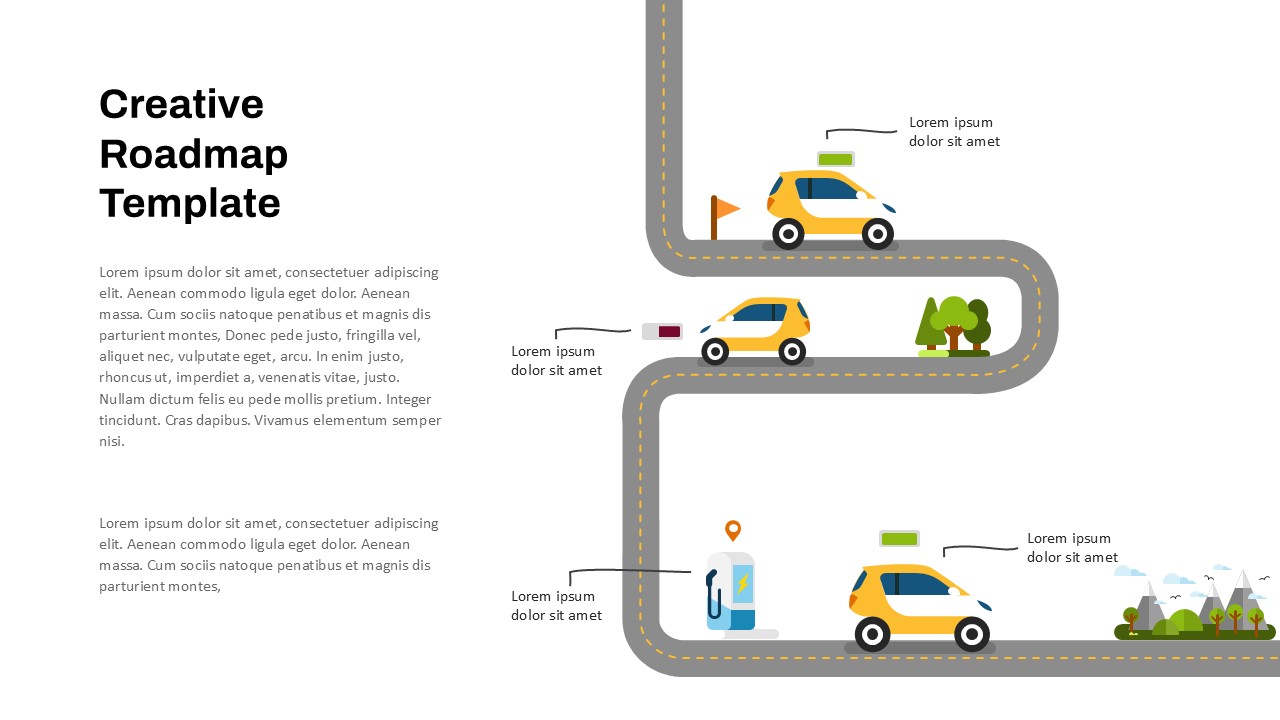
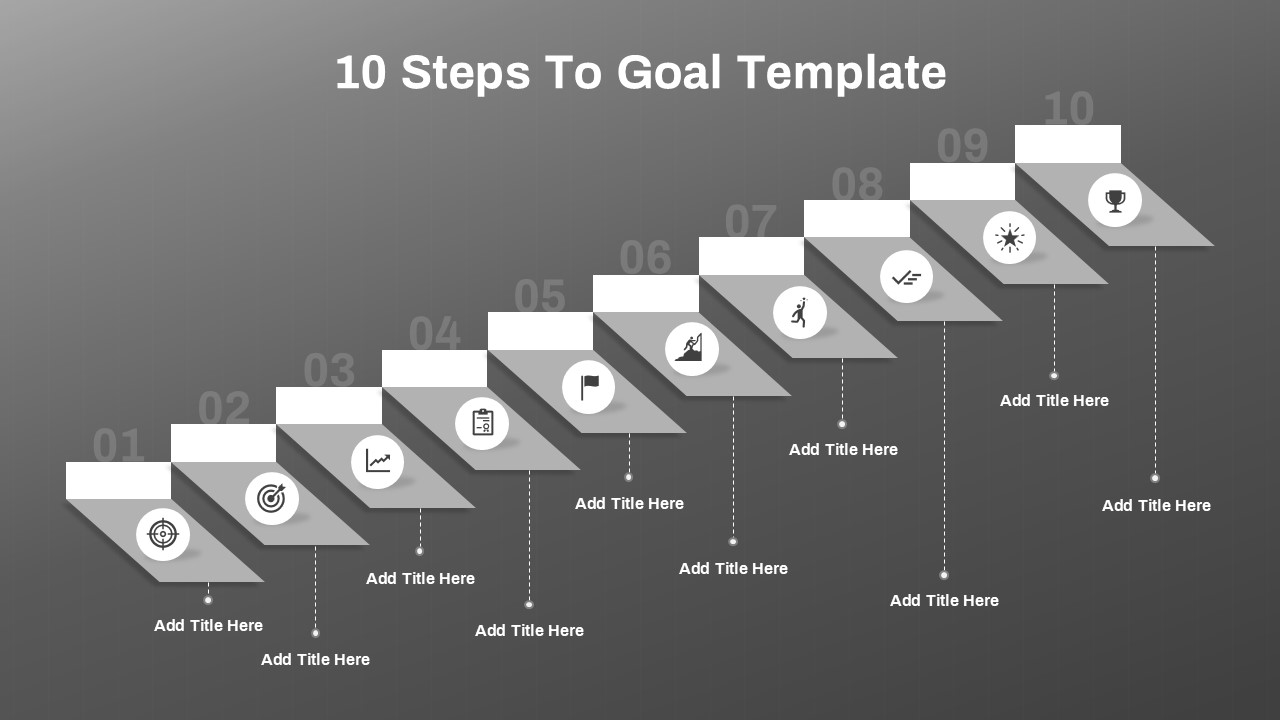
Cybersecurity Roadmap PPT Template
Develop a resilient and strategic defense framework with this Cybersecurity Roadmap Template PPT. Perfect for IT leaders, security analysts, and compliance teams, this visually dynamic roadmap slide in powerpoint provides a clear, step-by-step roadmap to implement and improve an organization’s cybersecurity posture.
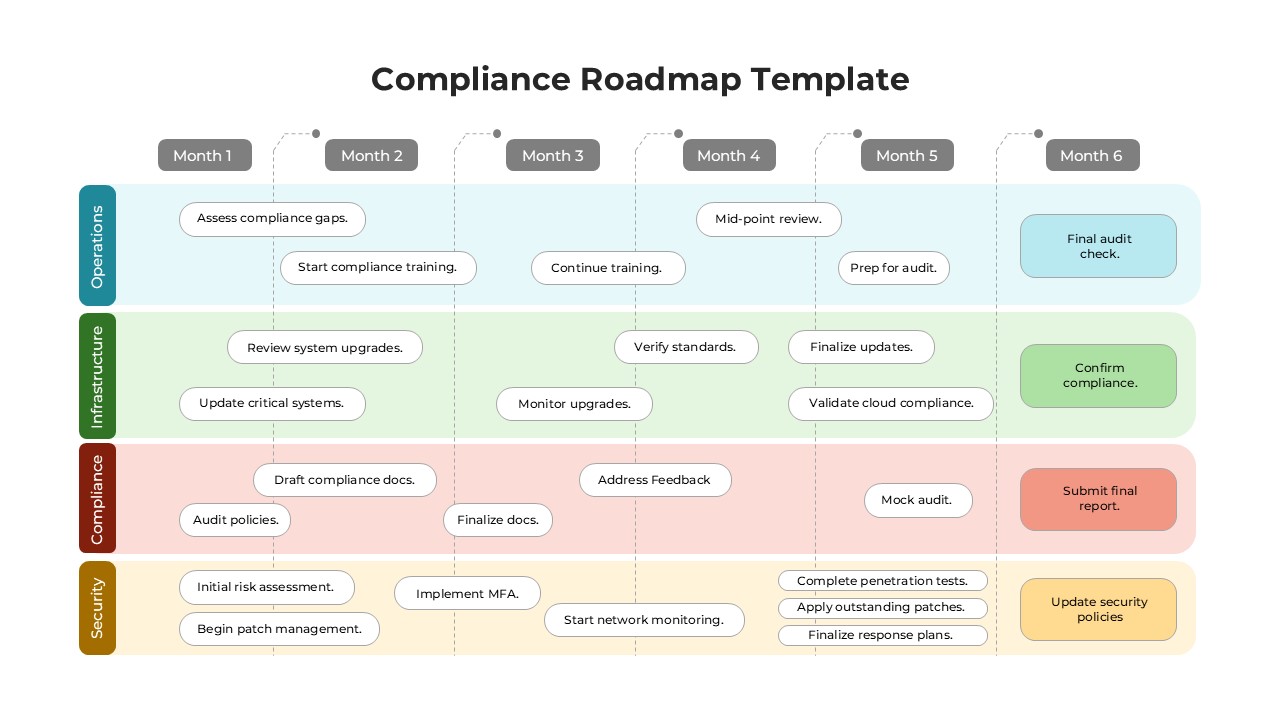
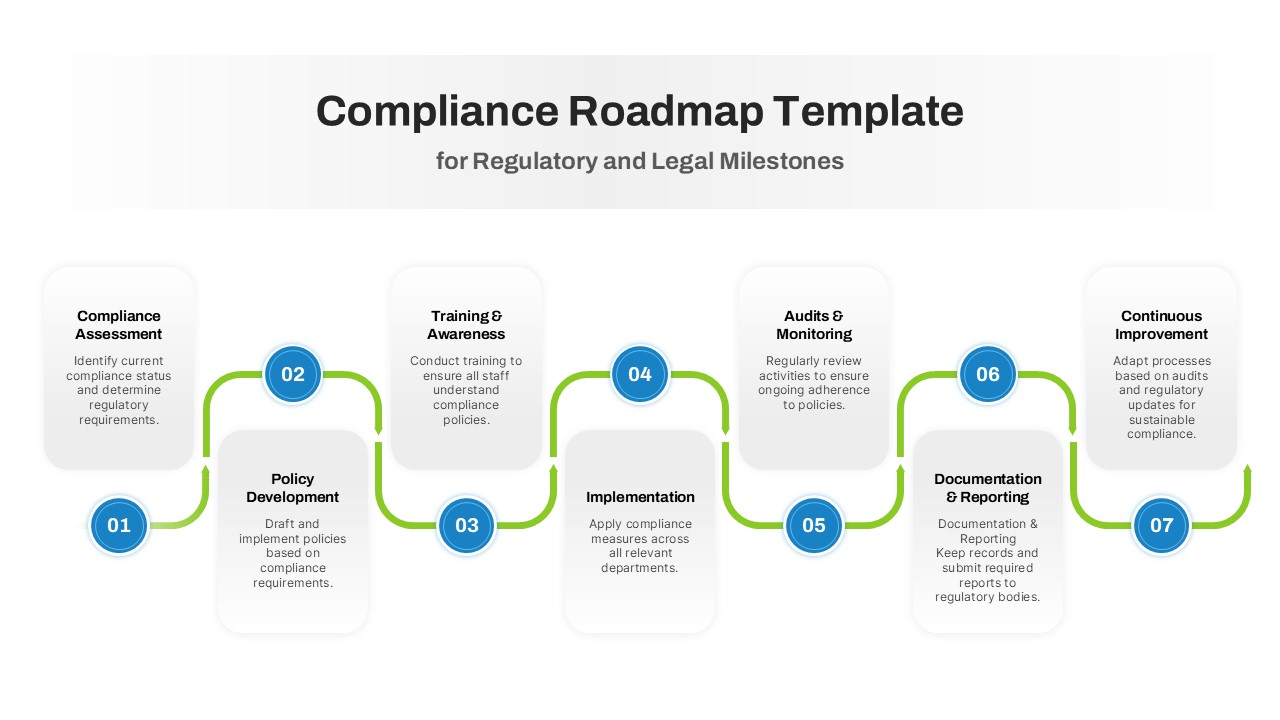
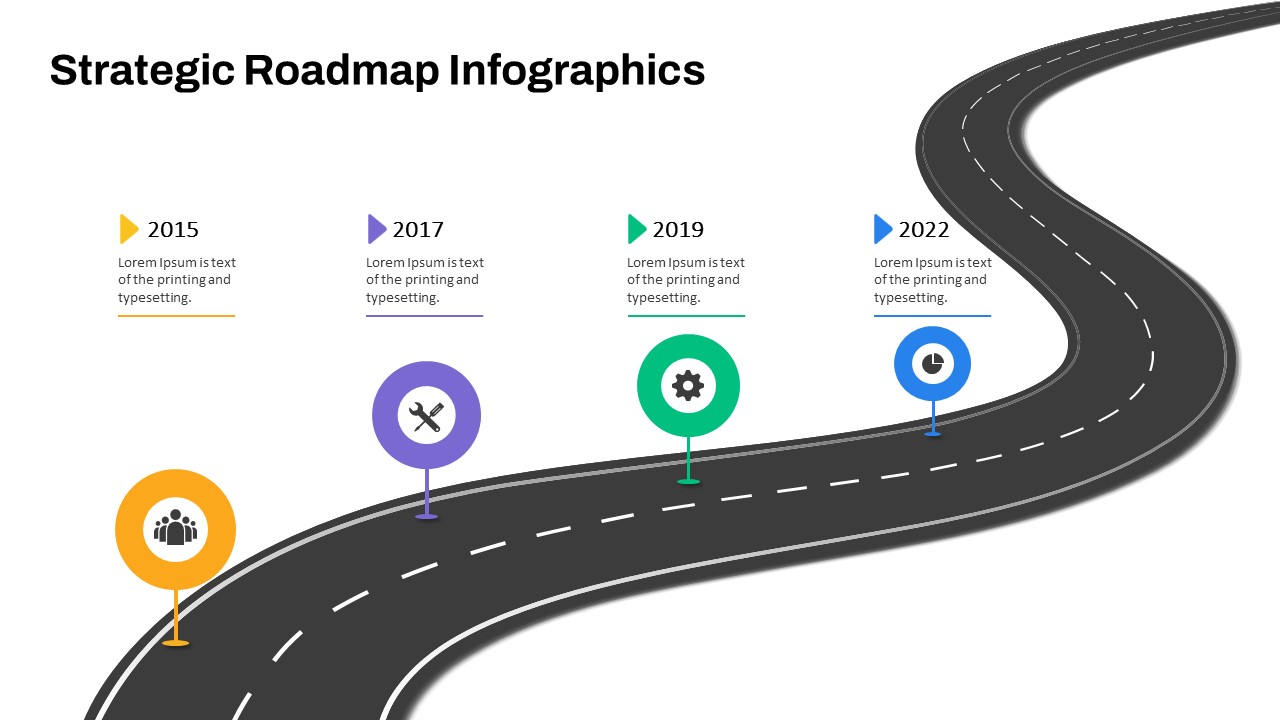
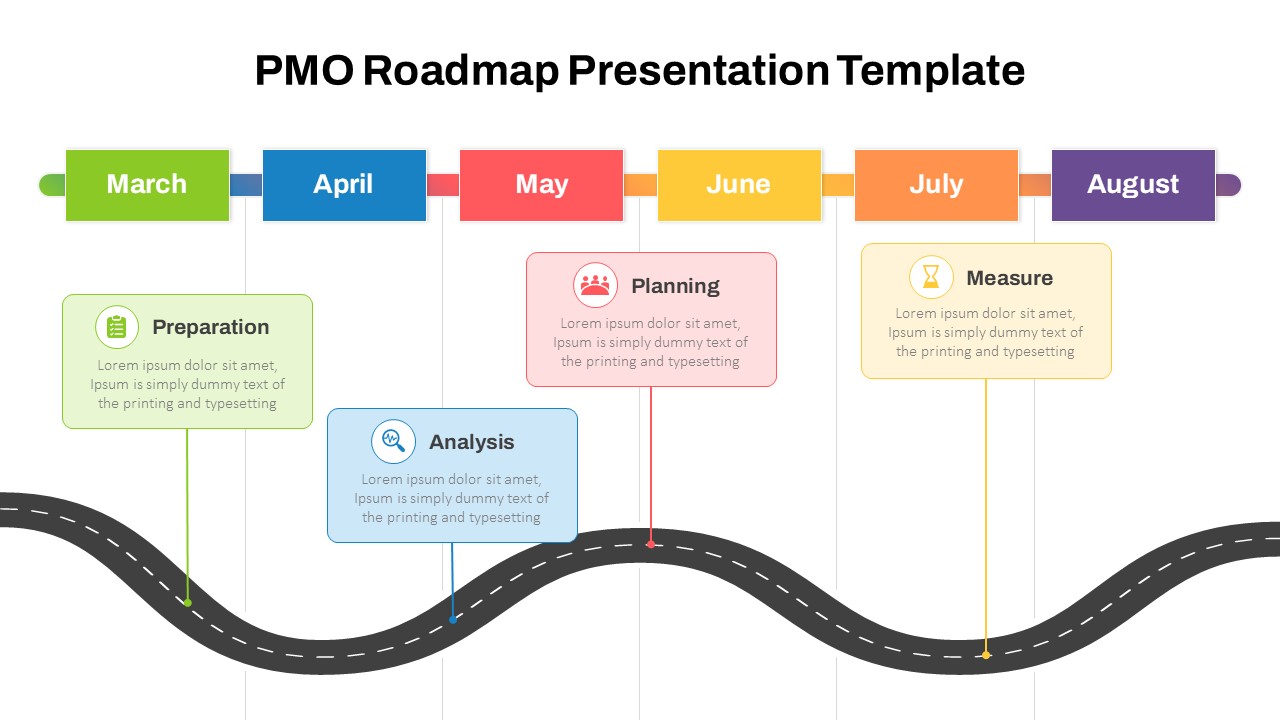
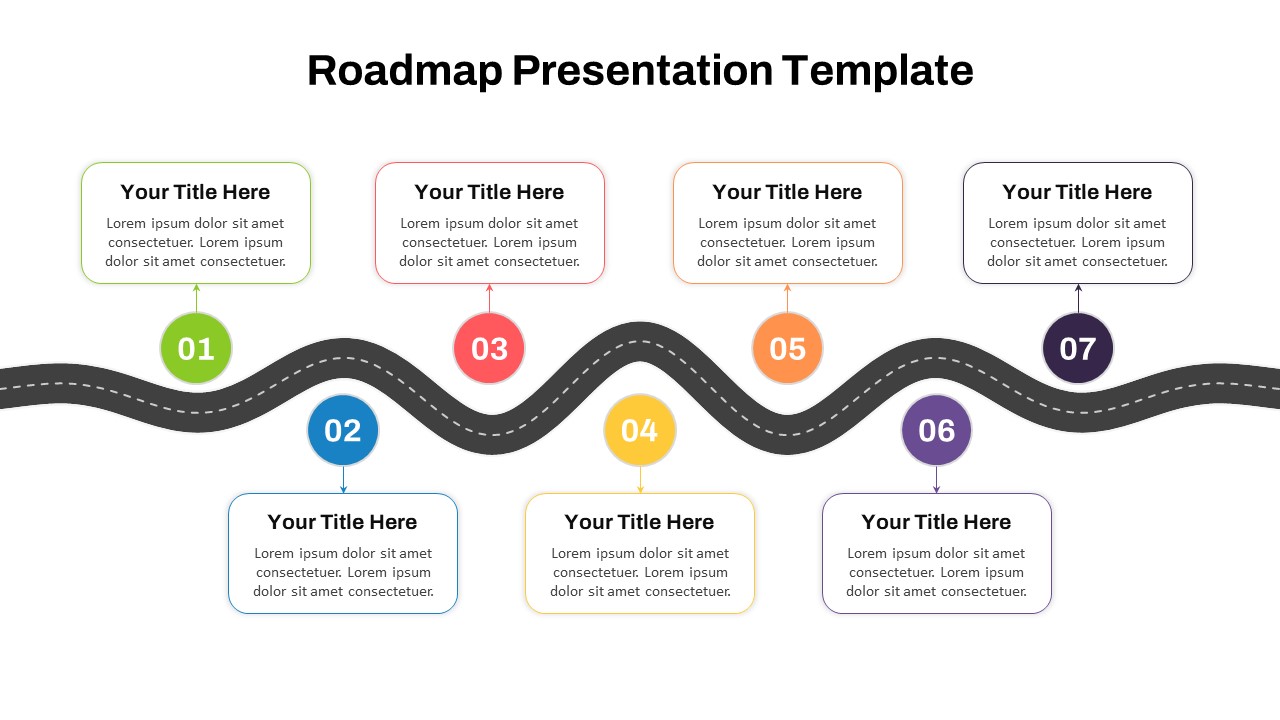
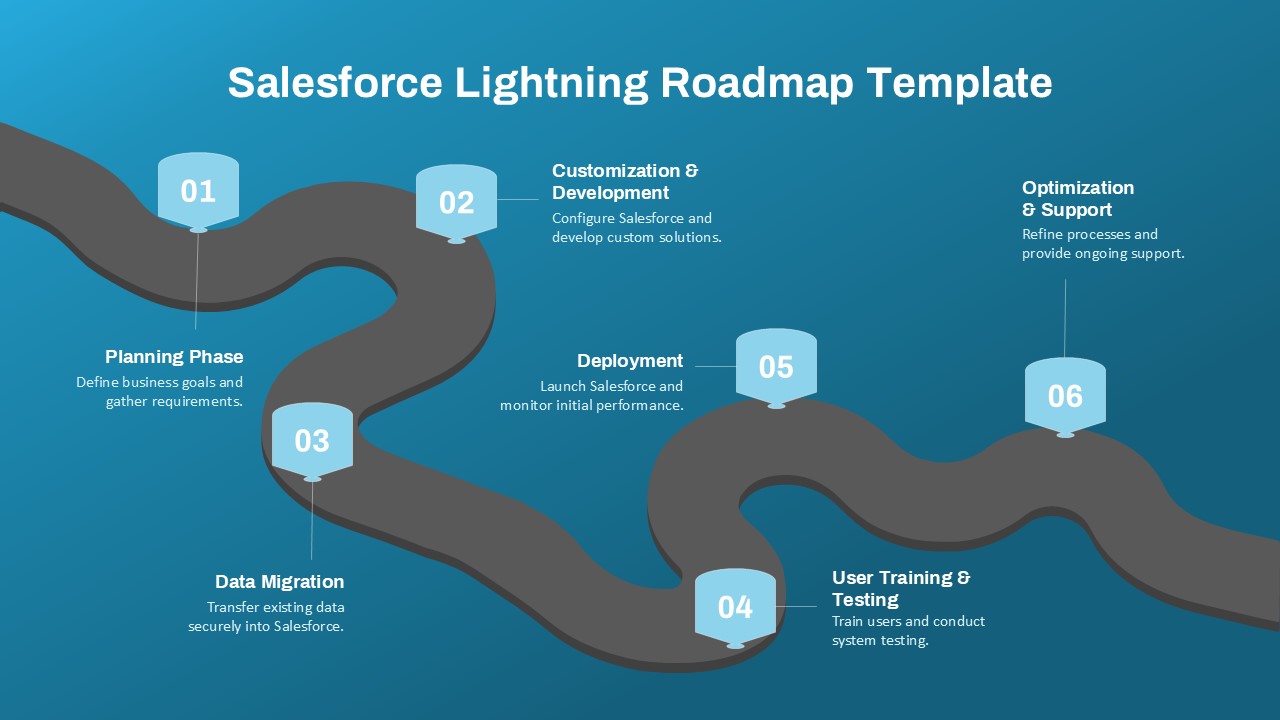
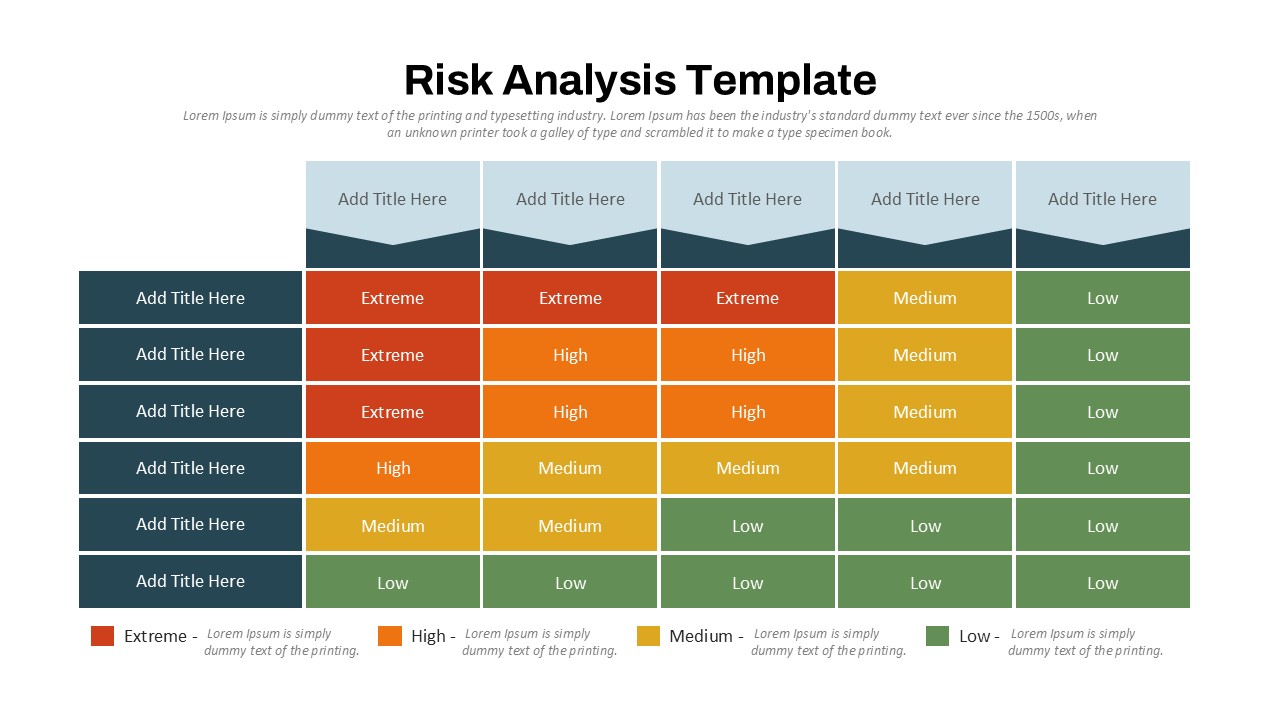
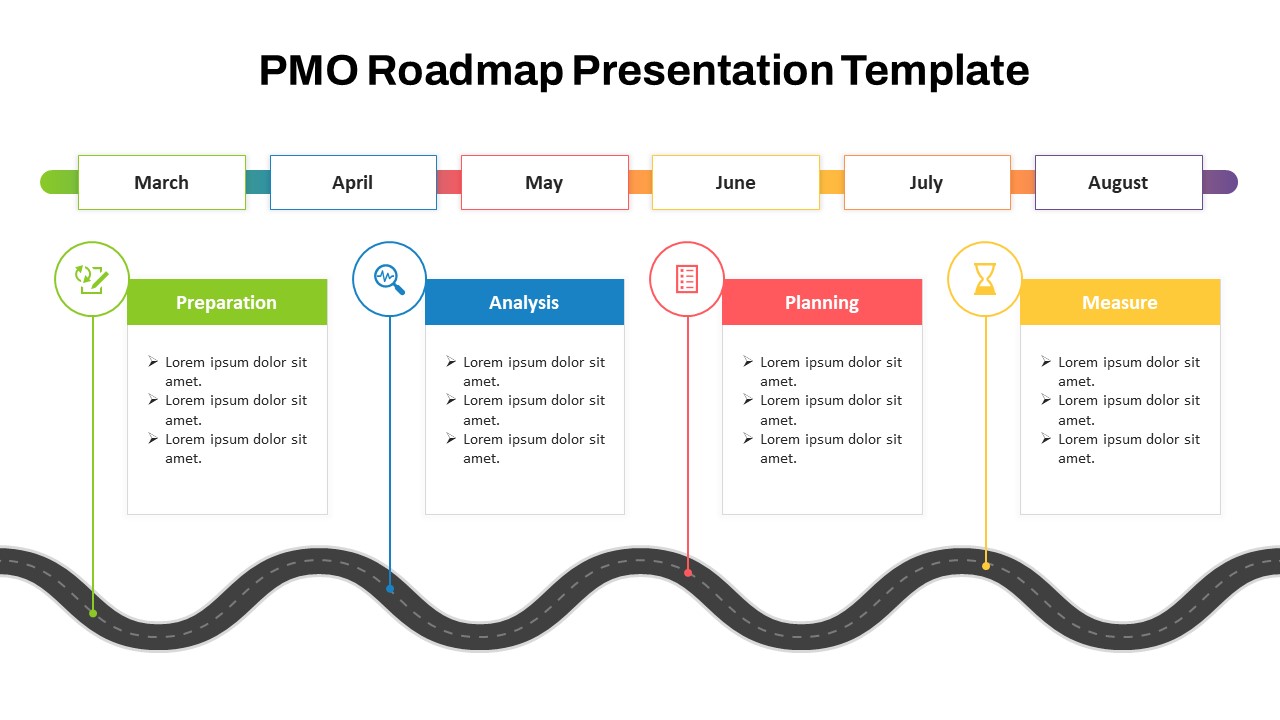
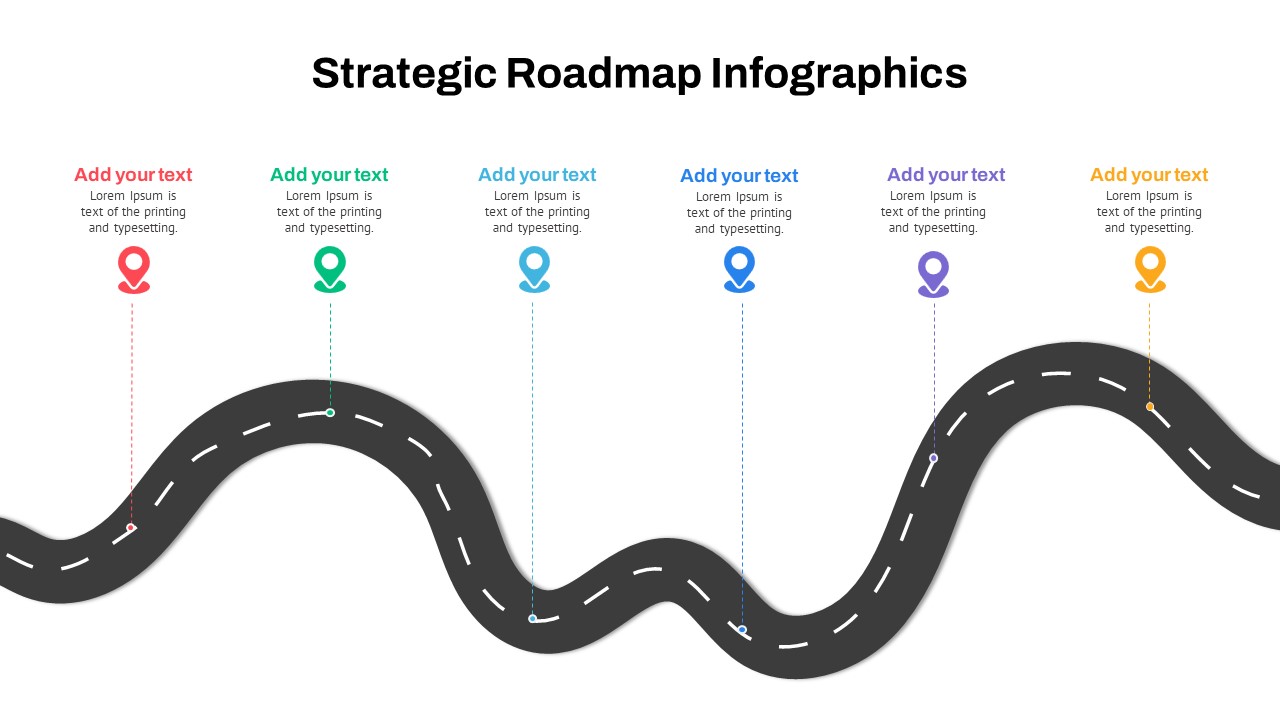
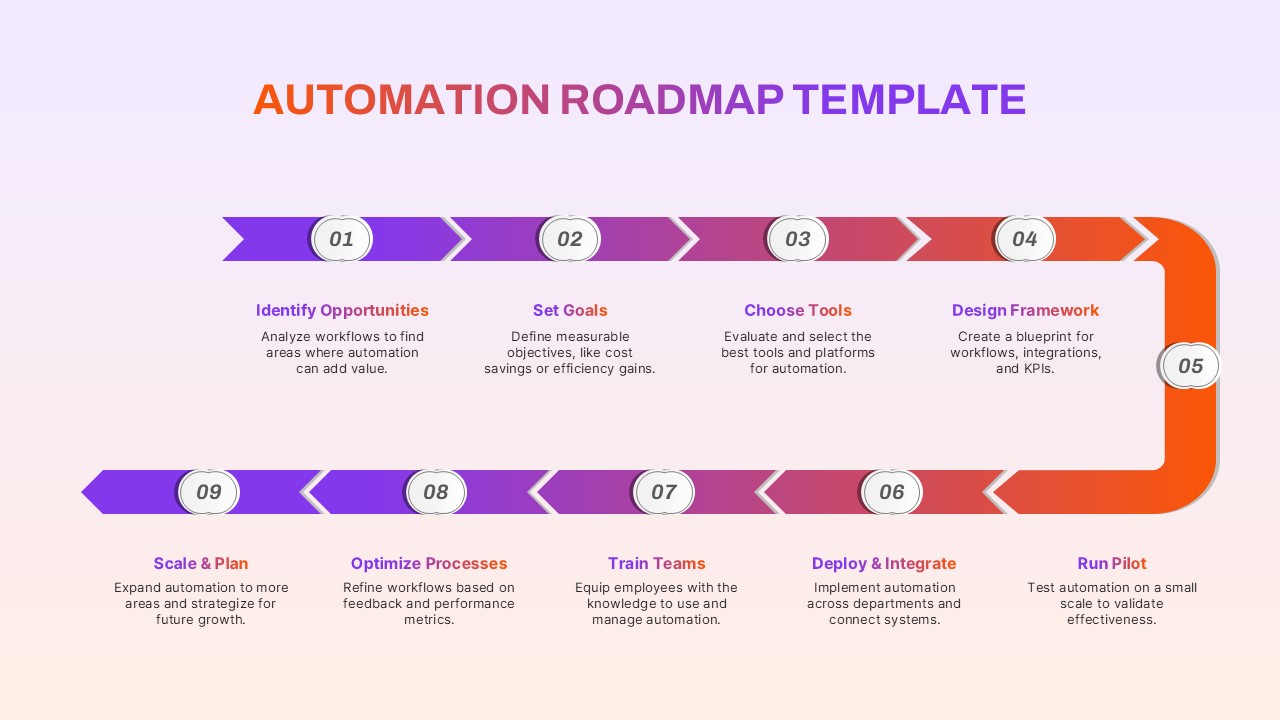
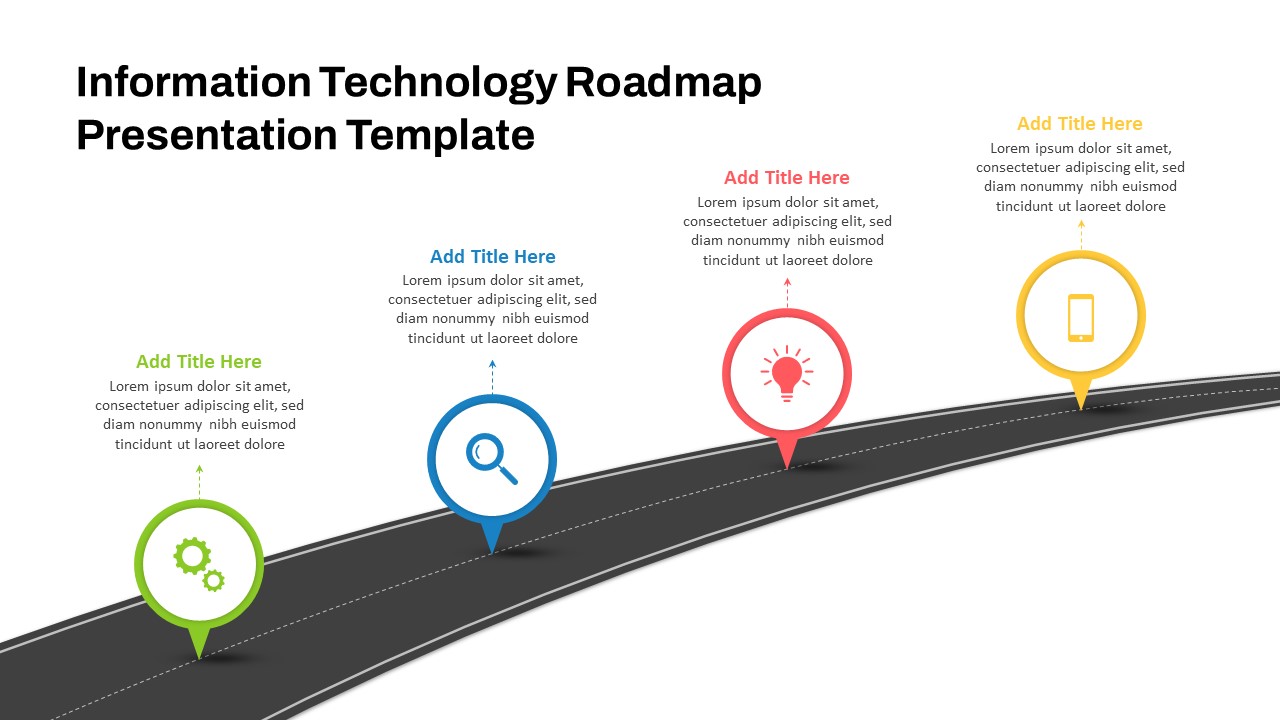
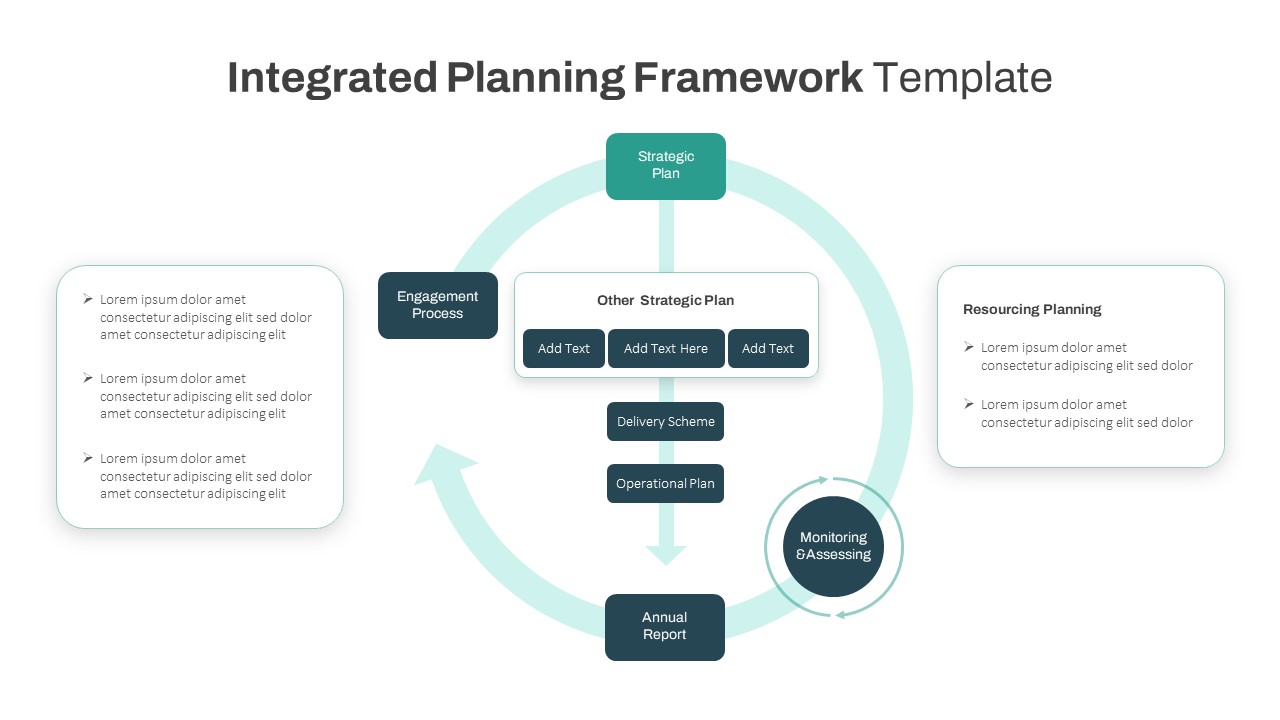
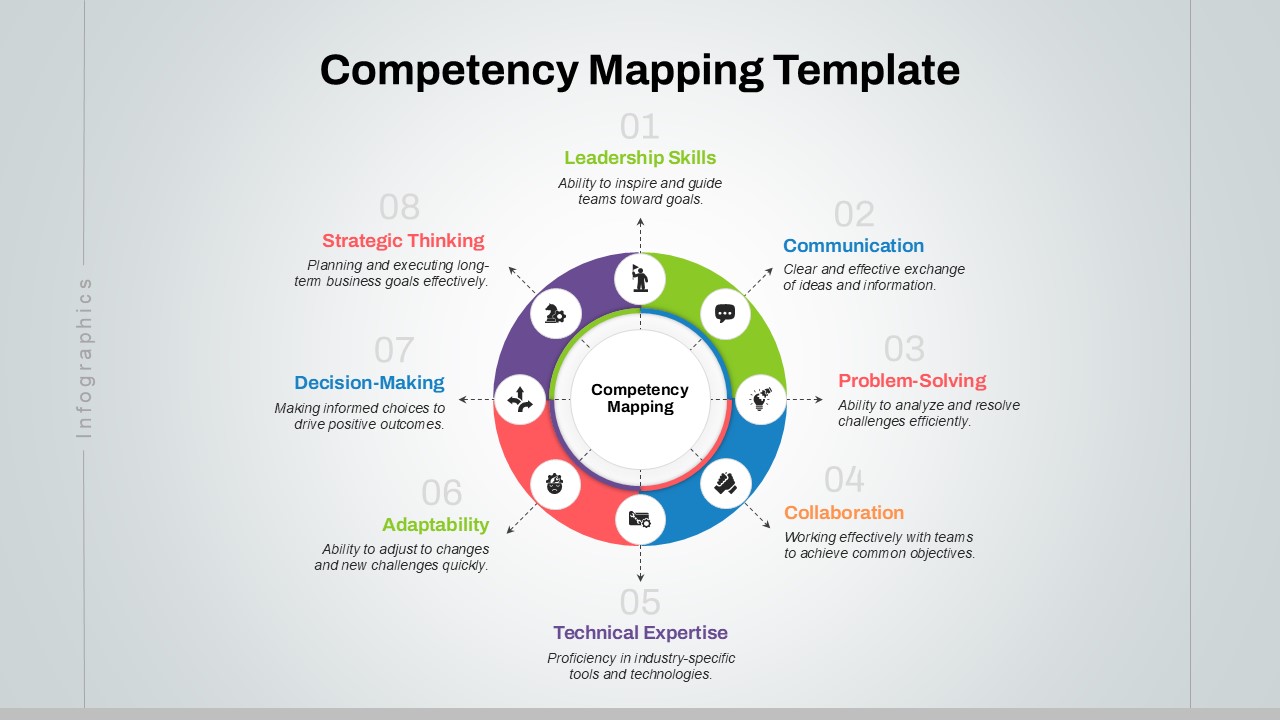
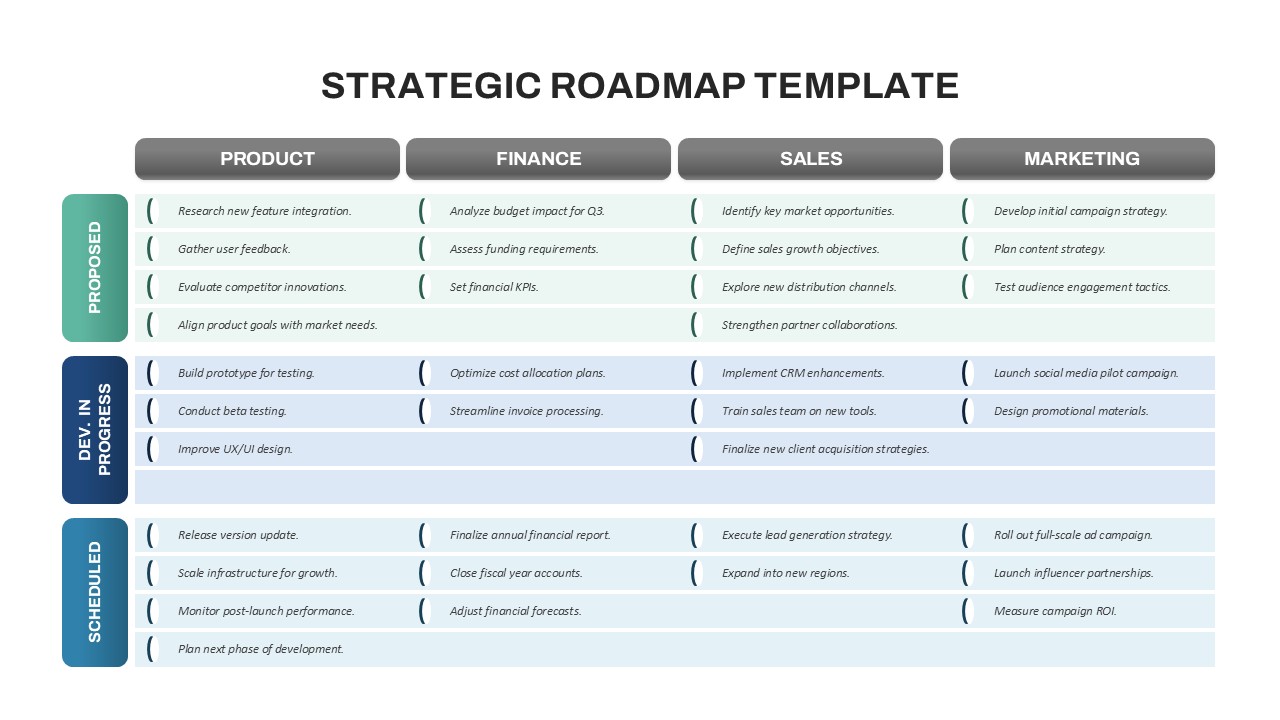
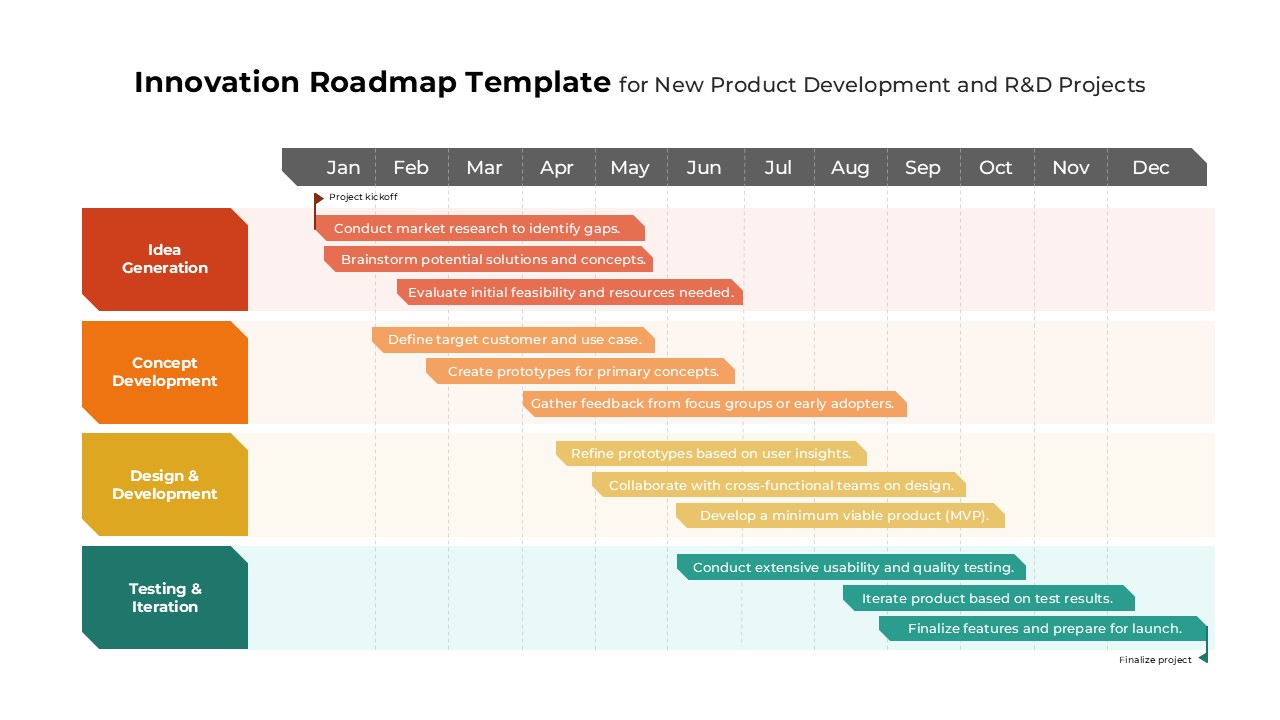
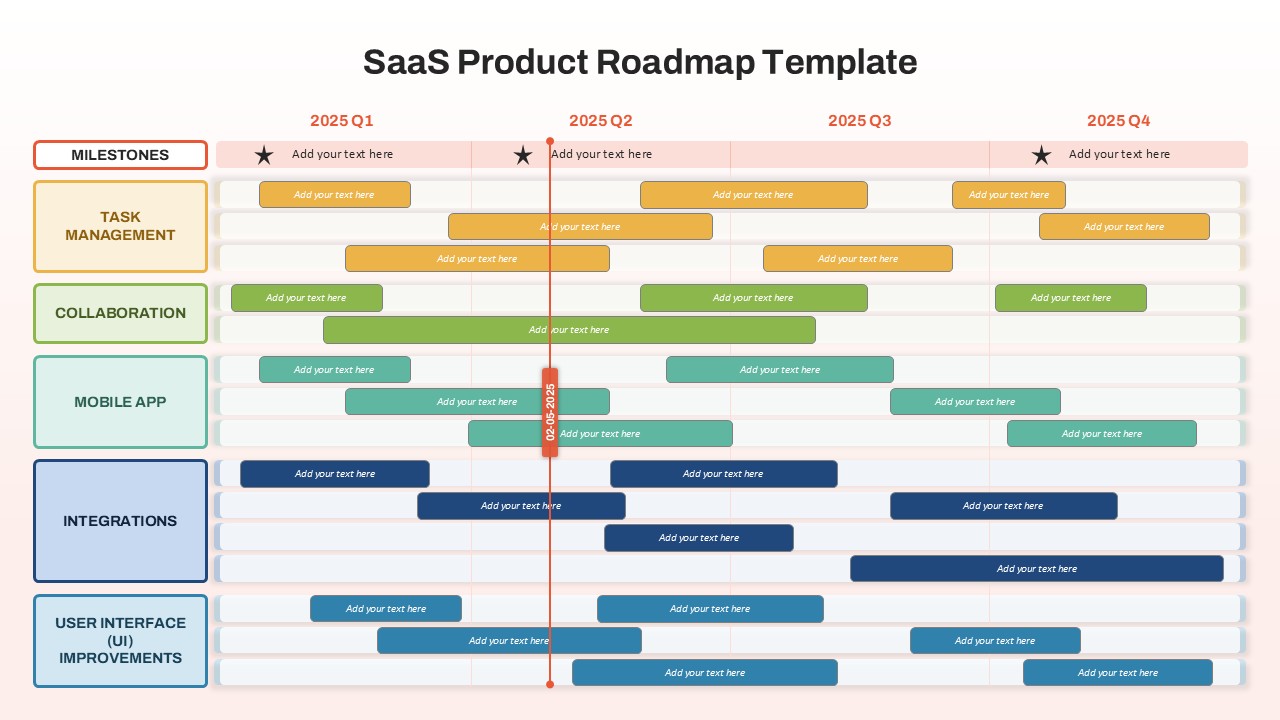
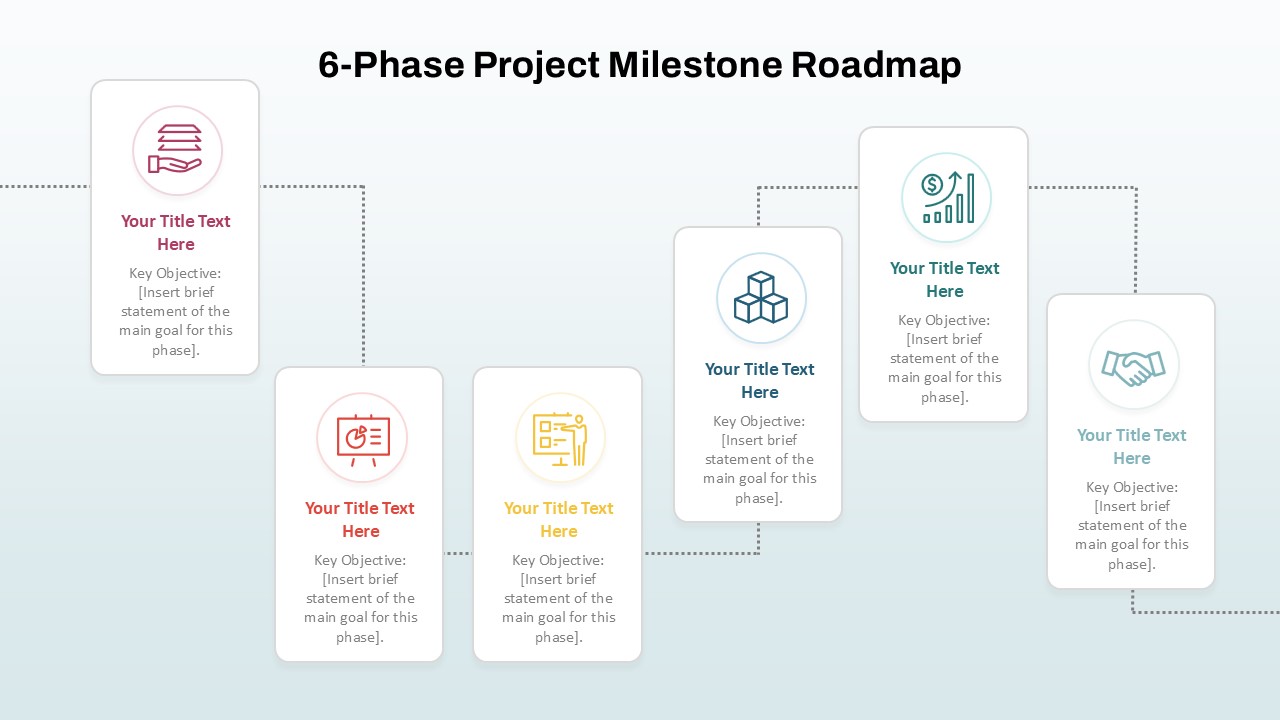
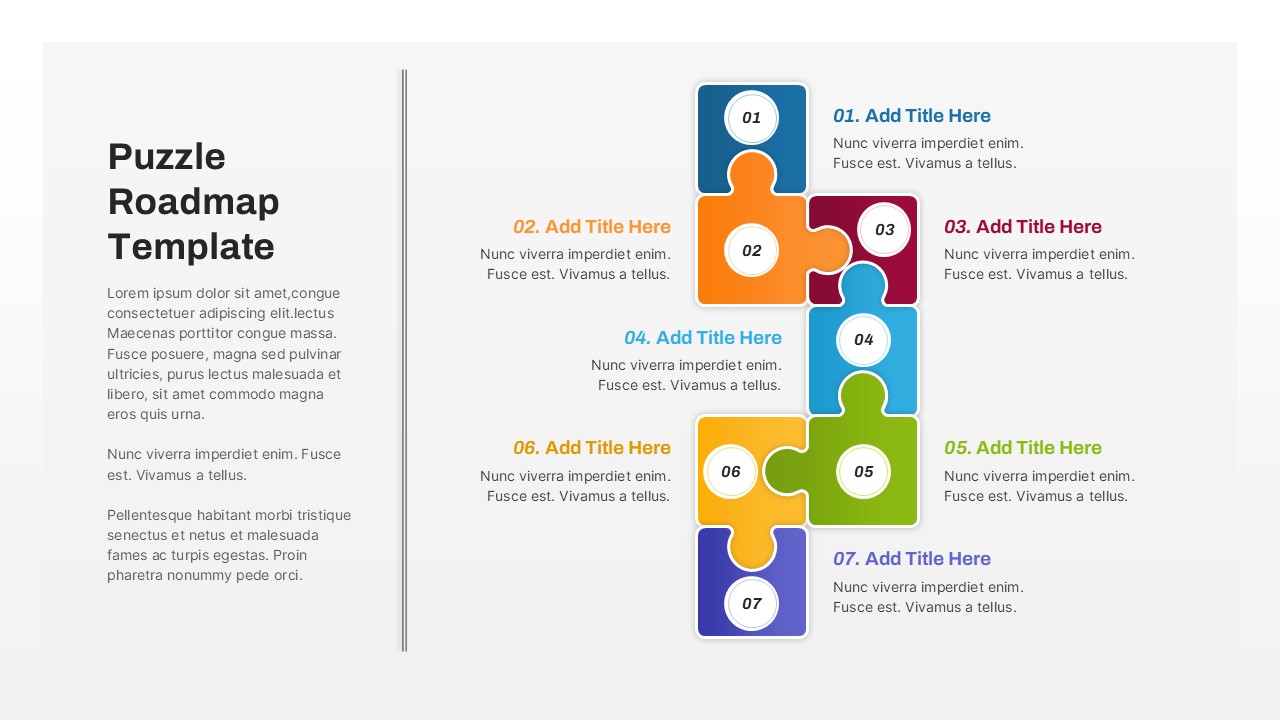
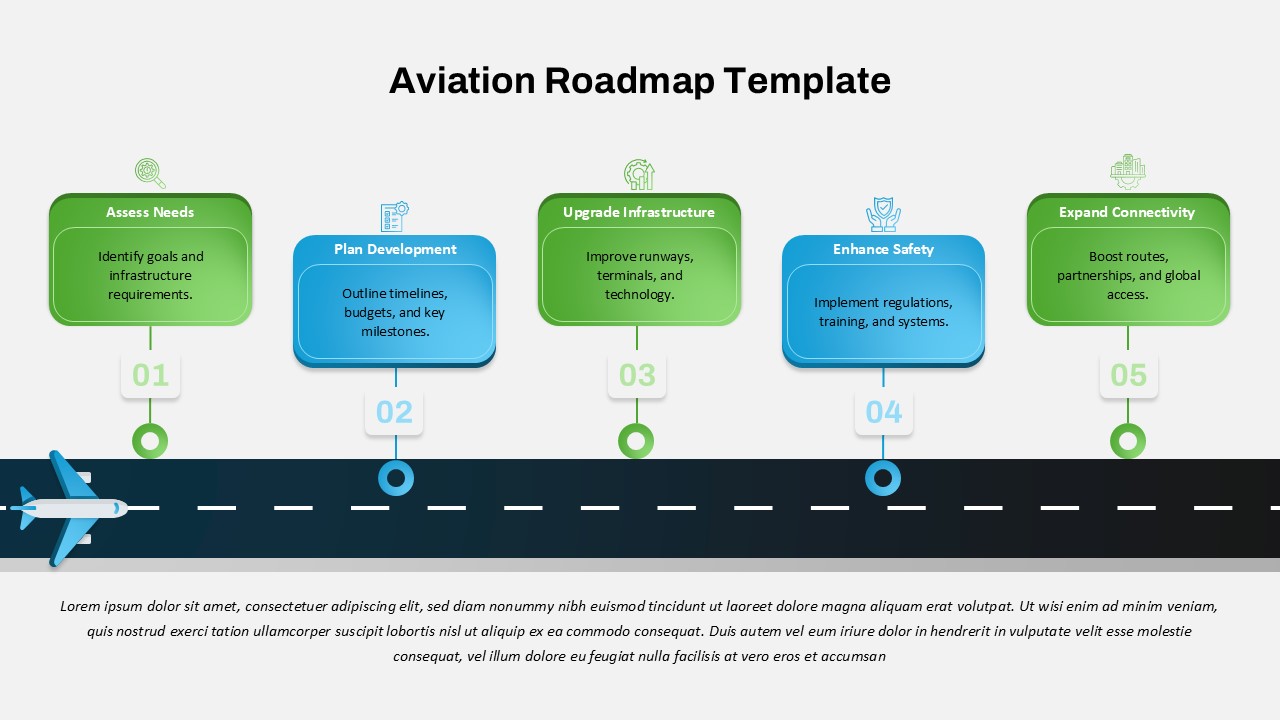
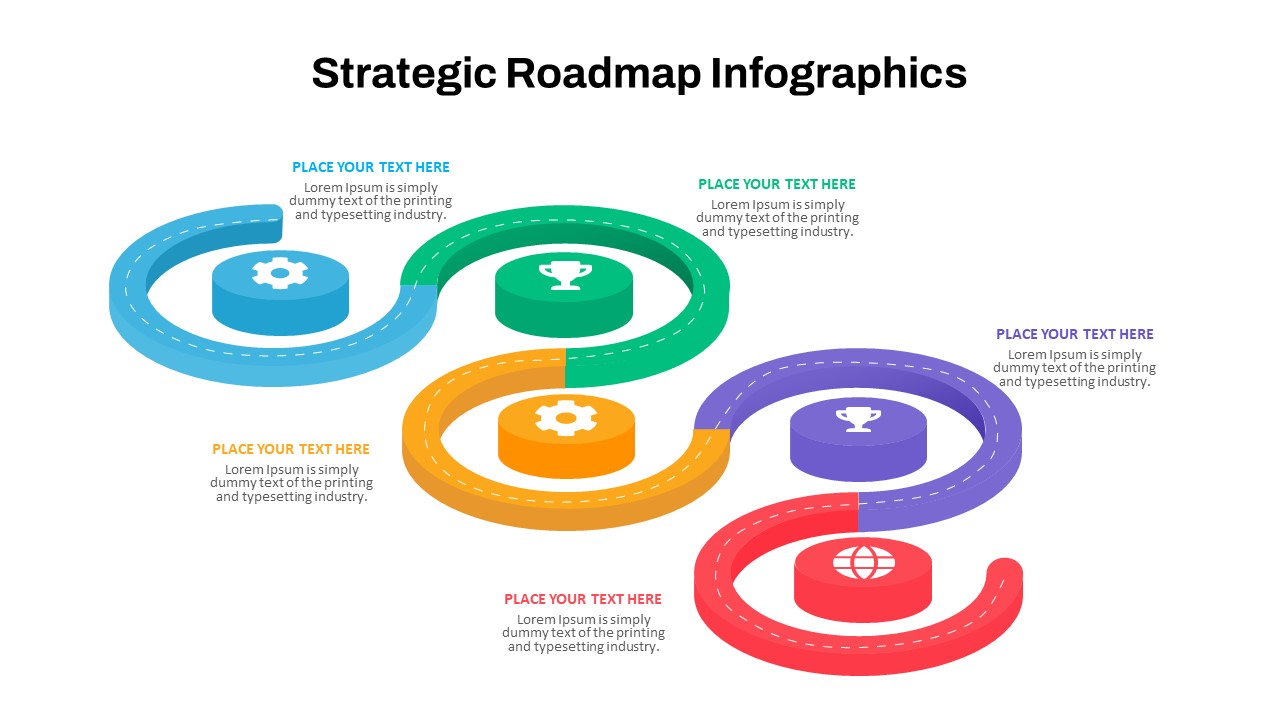
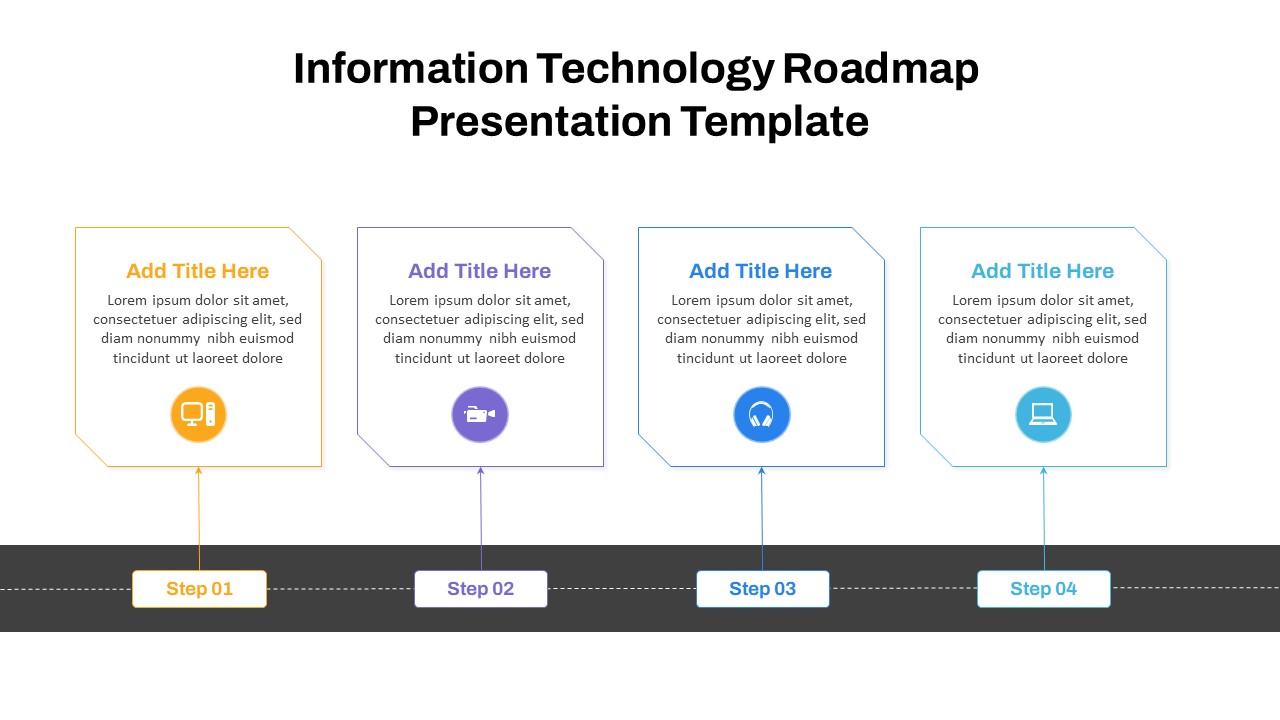
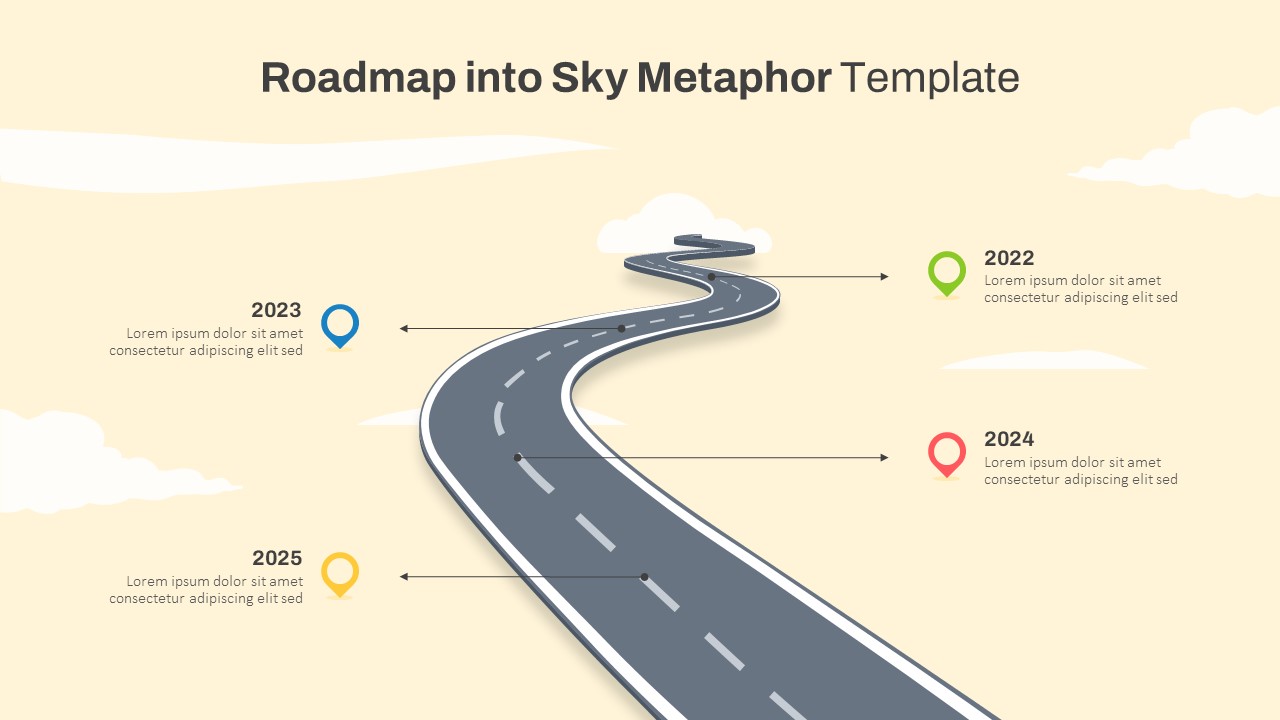
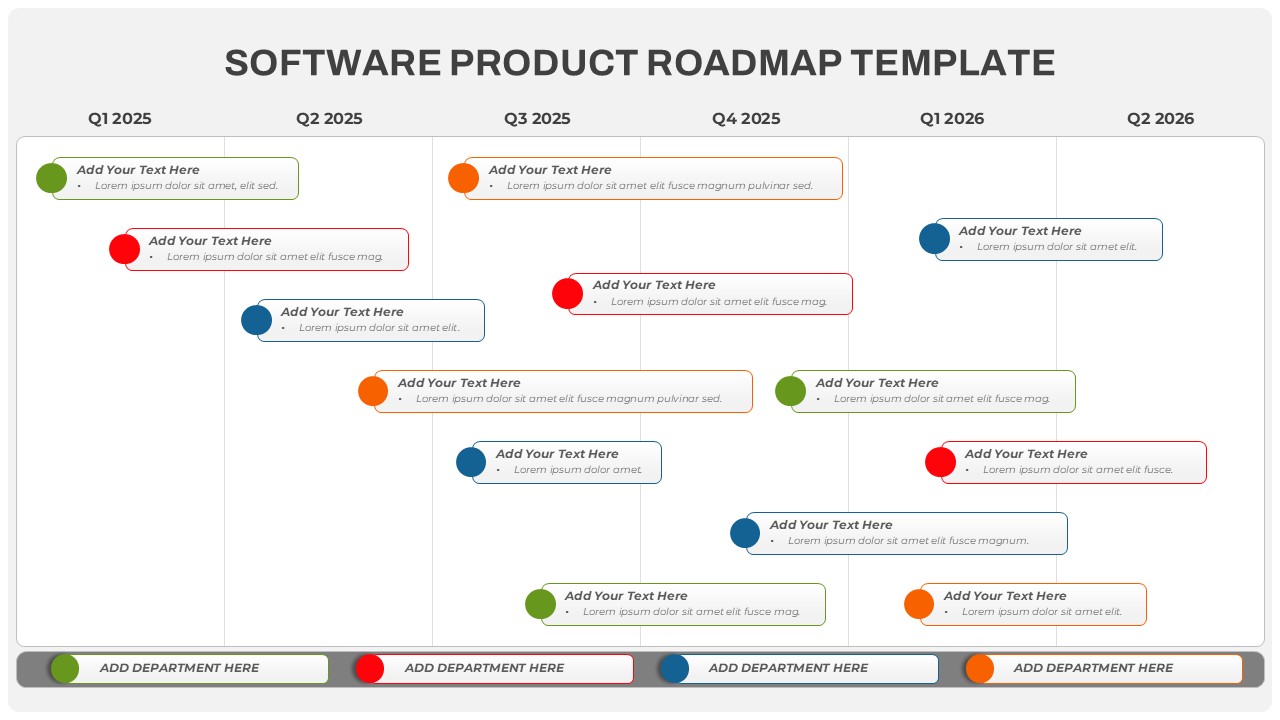
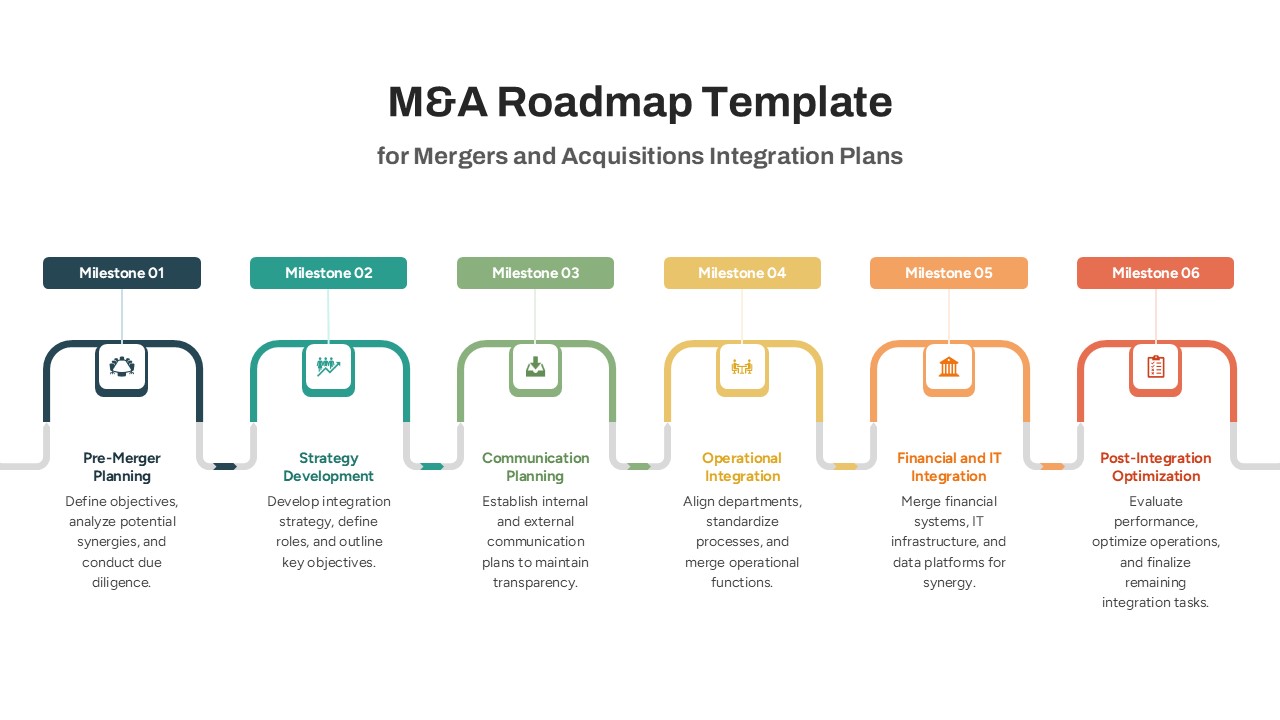
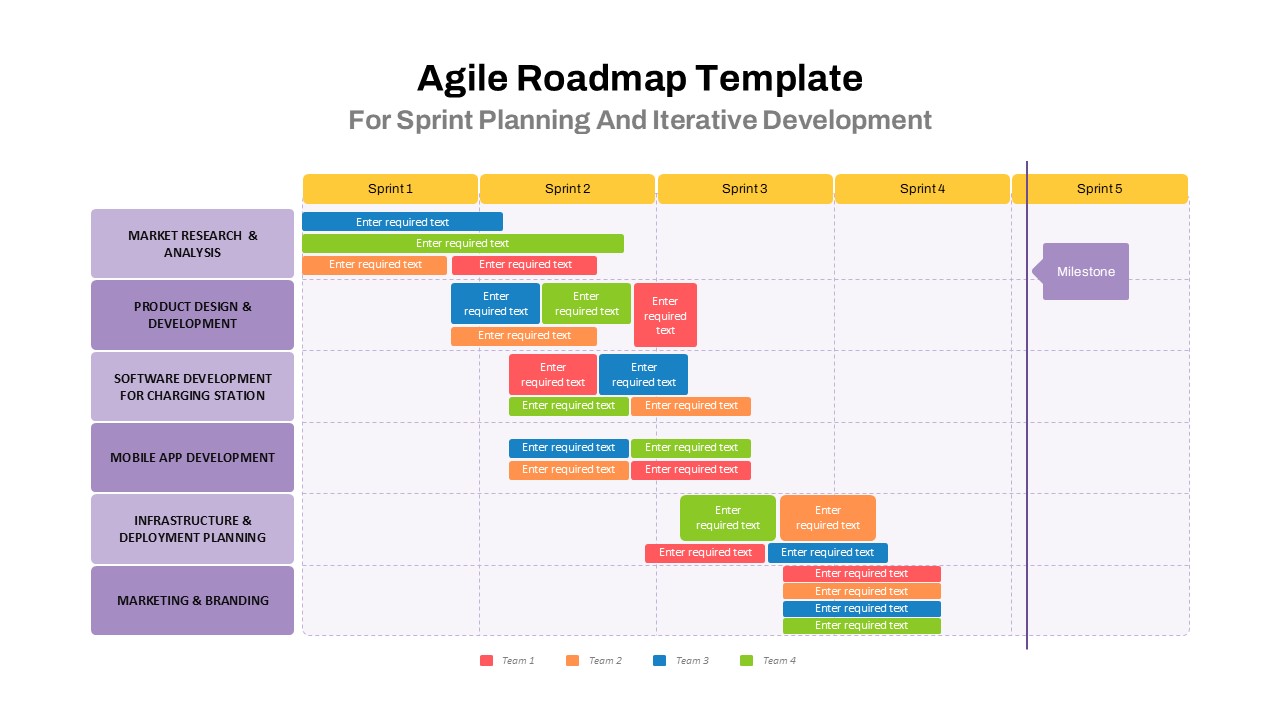
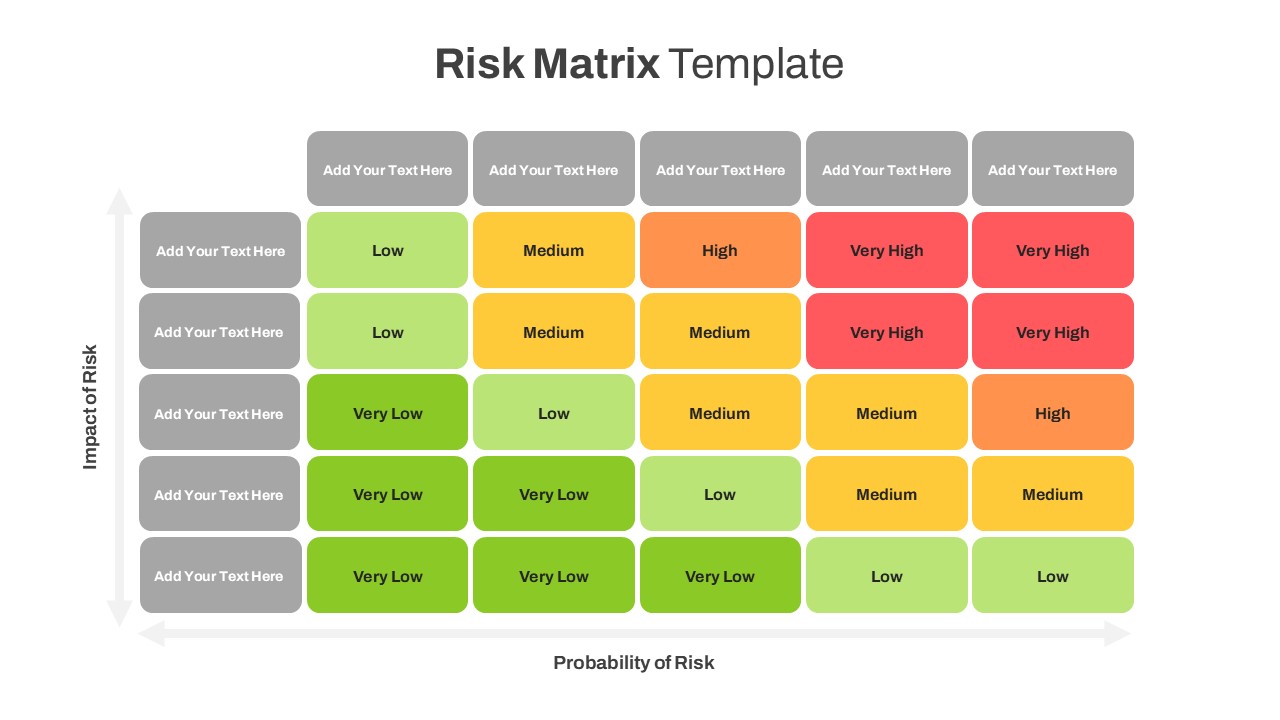
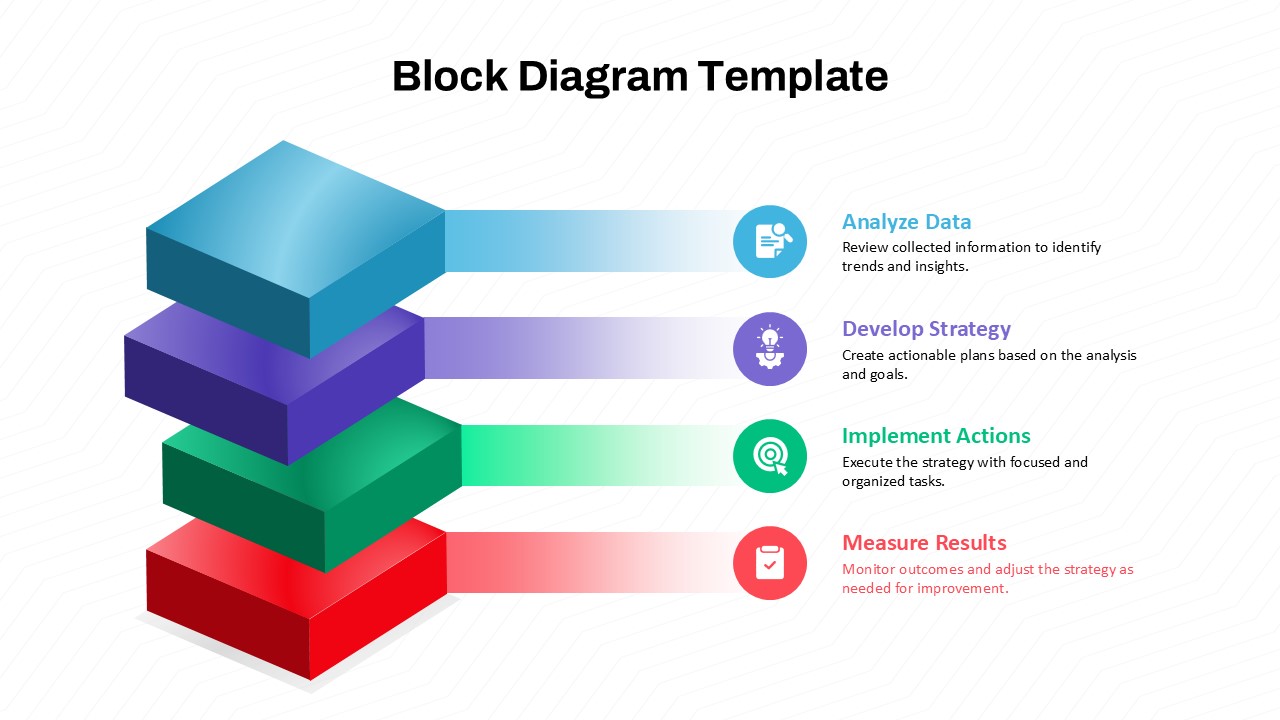
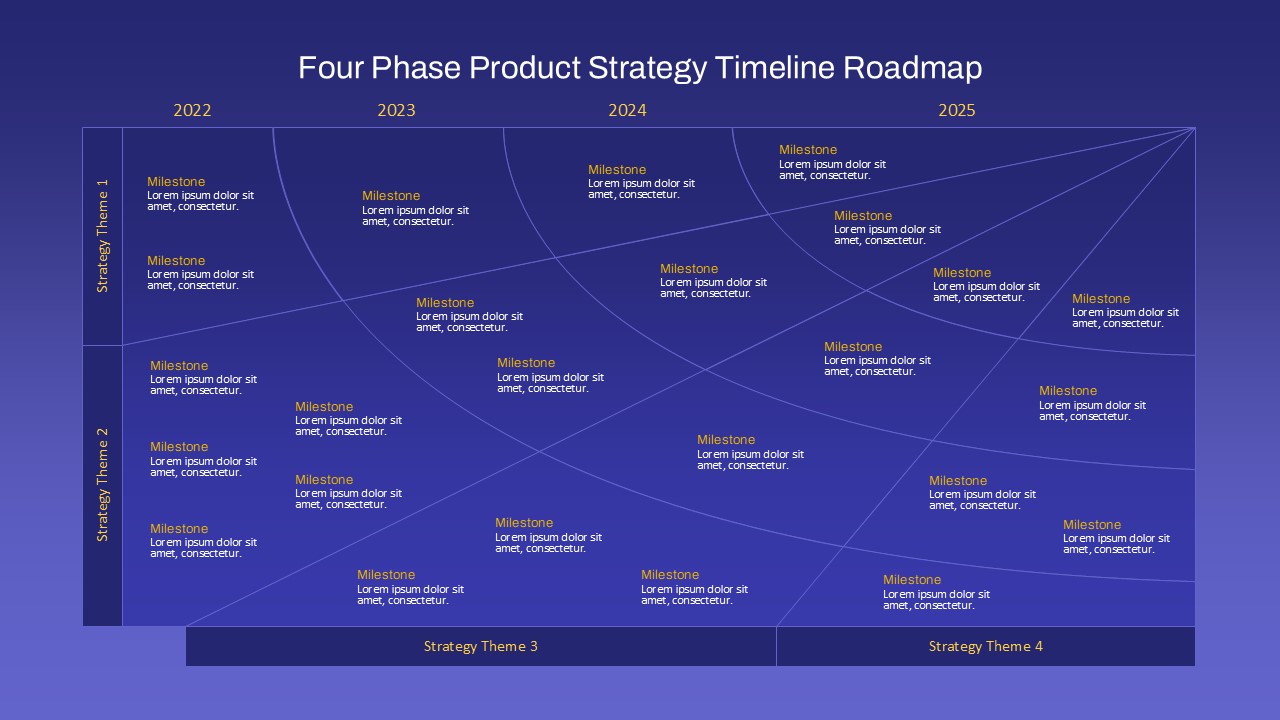
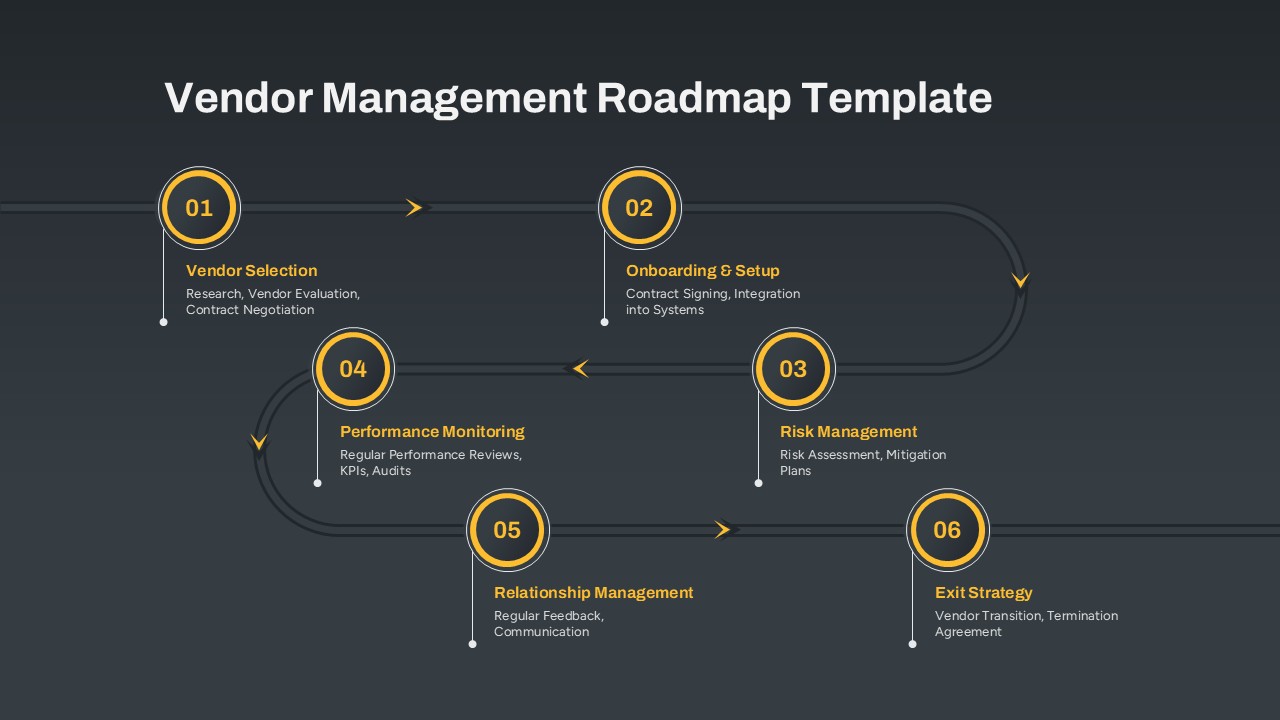
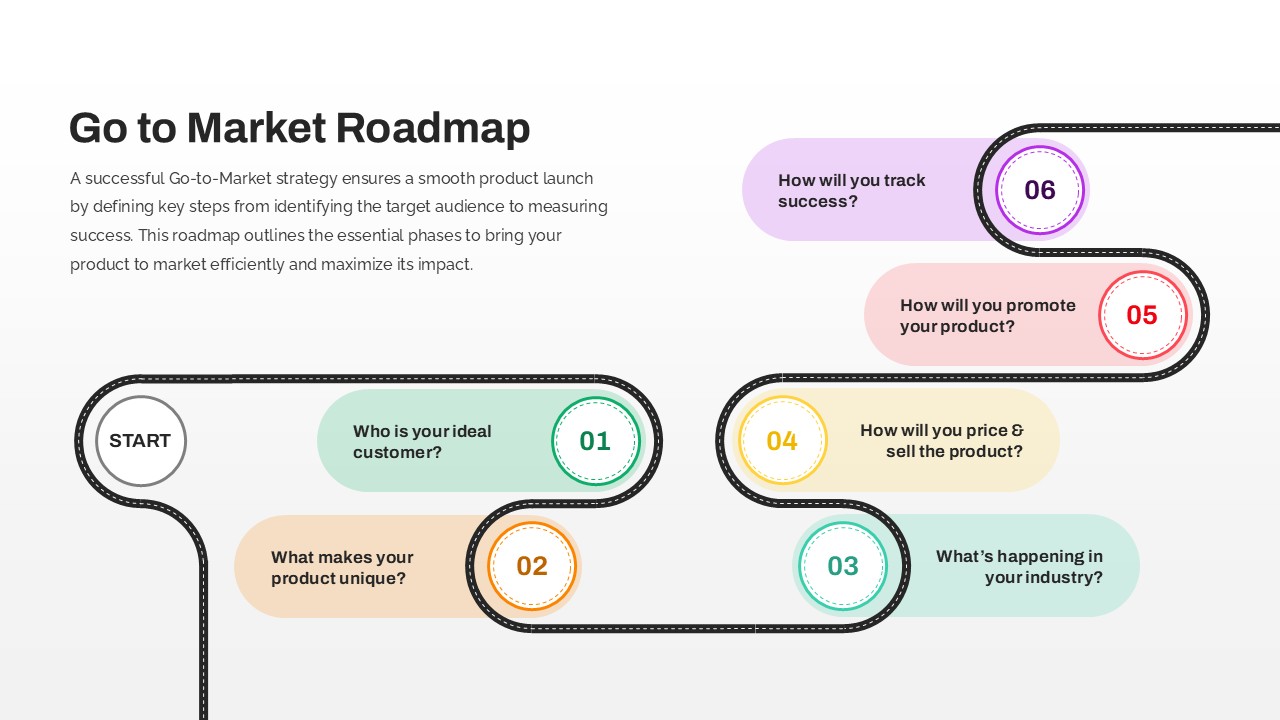
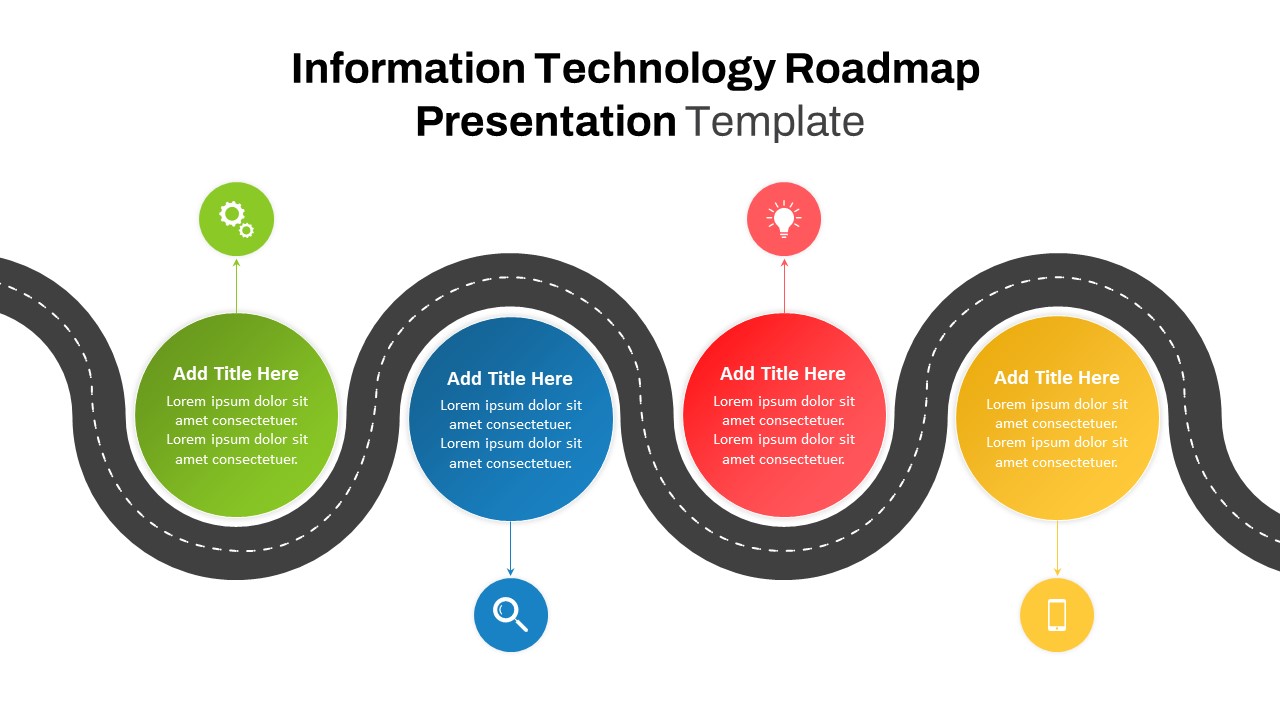
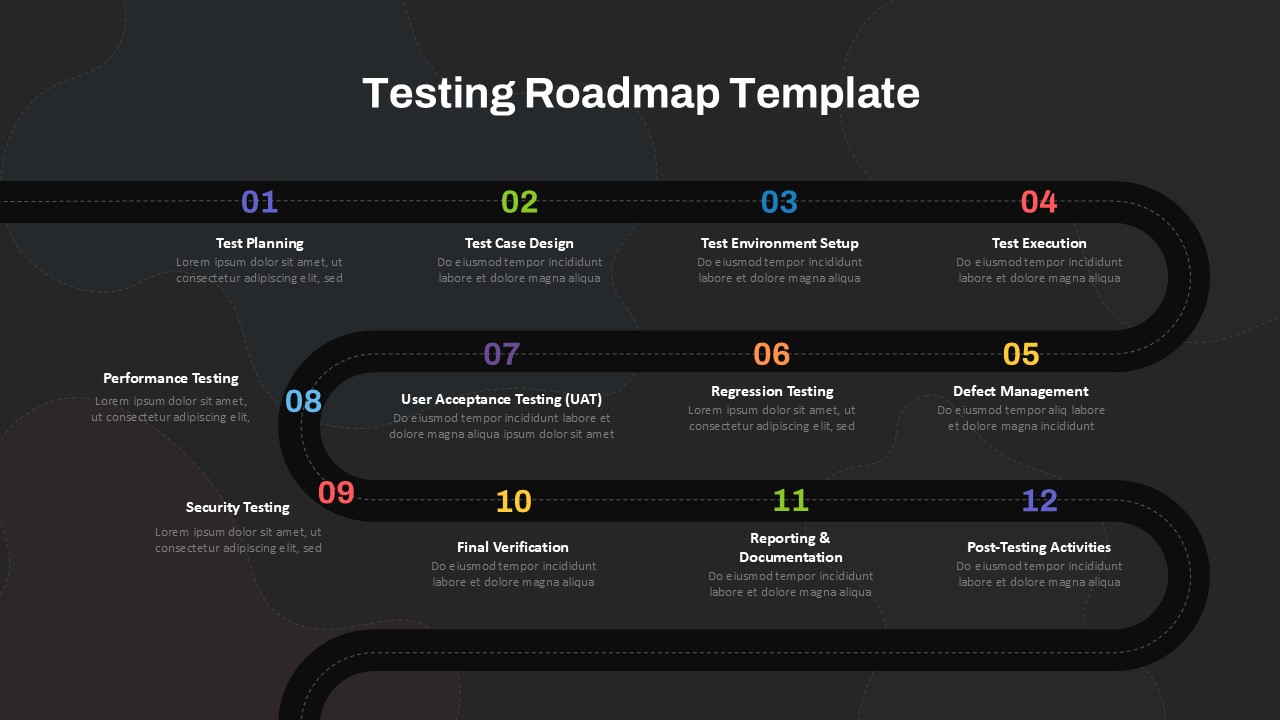
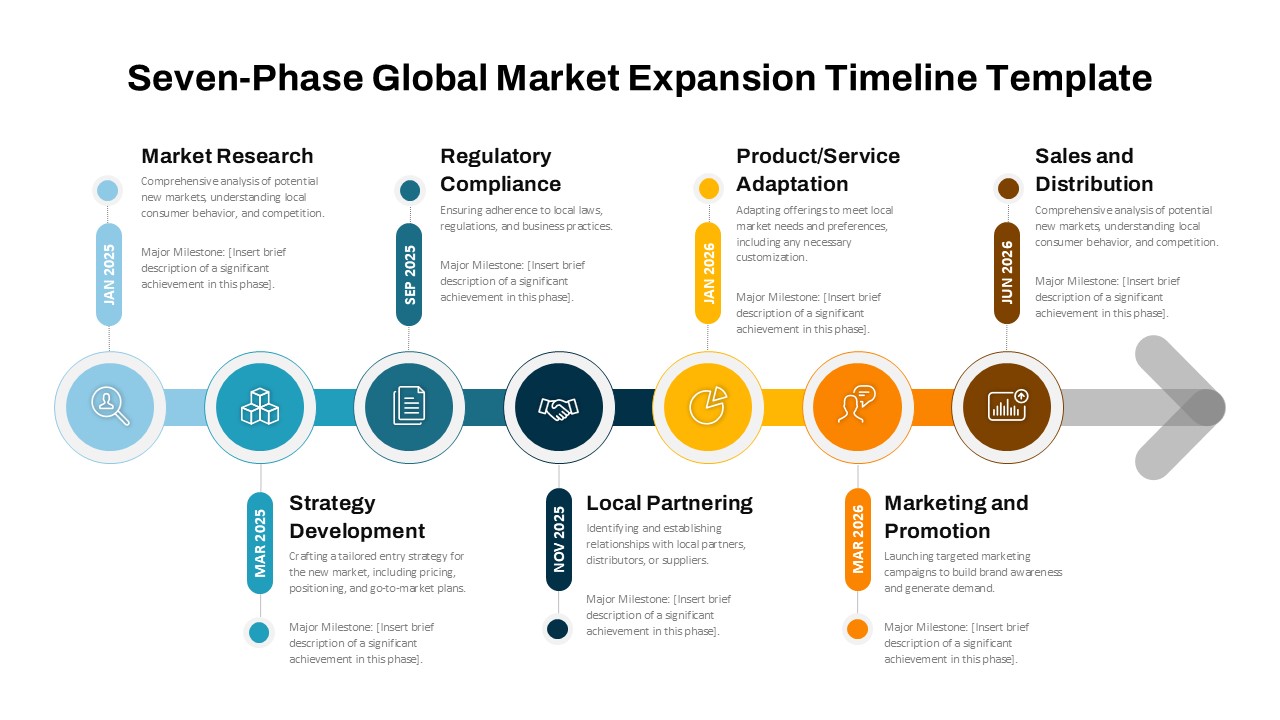
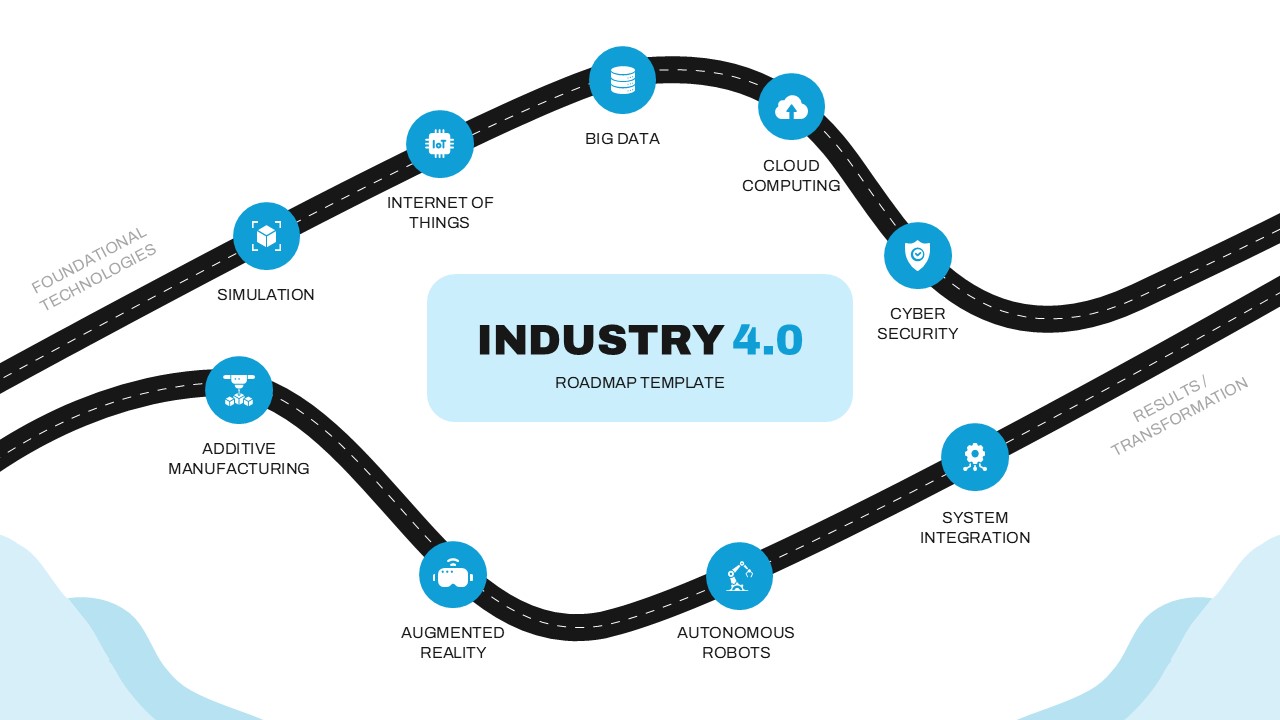
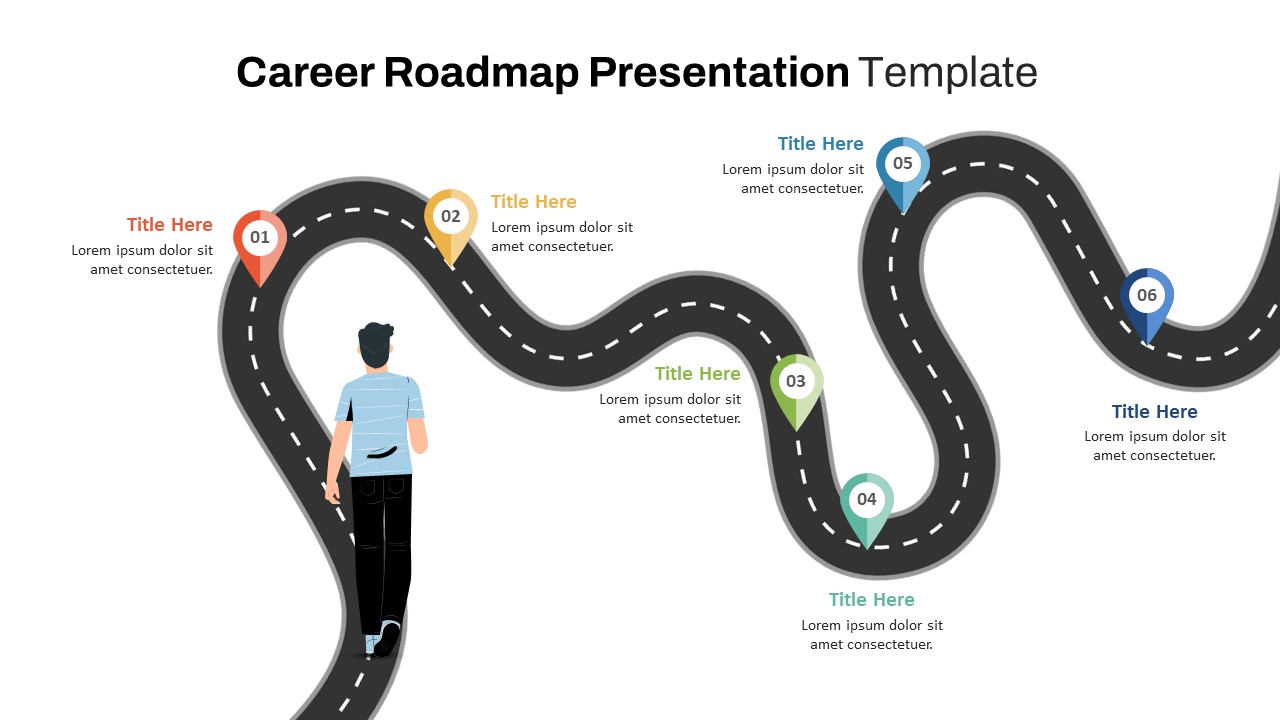
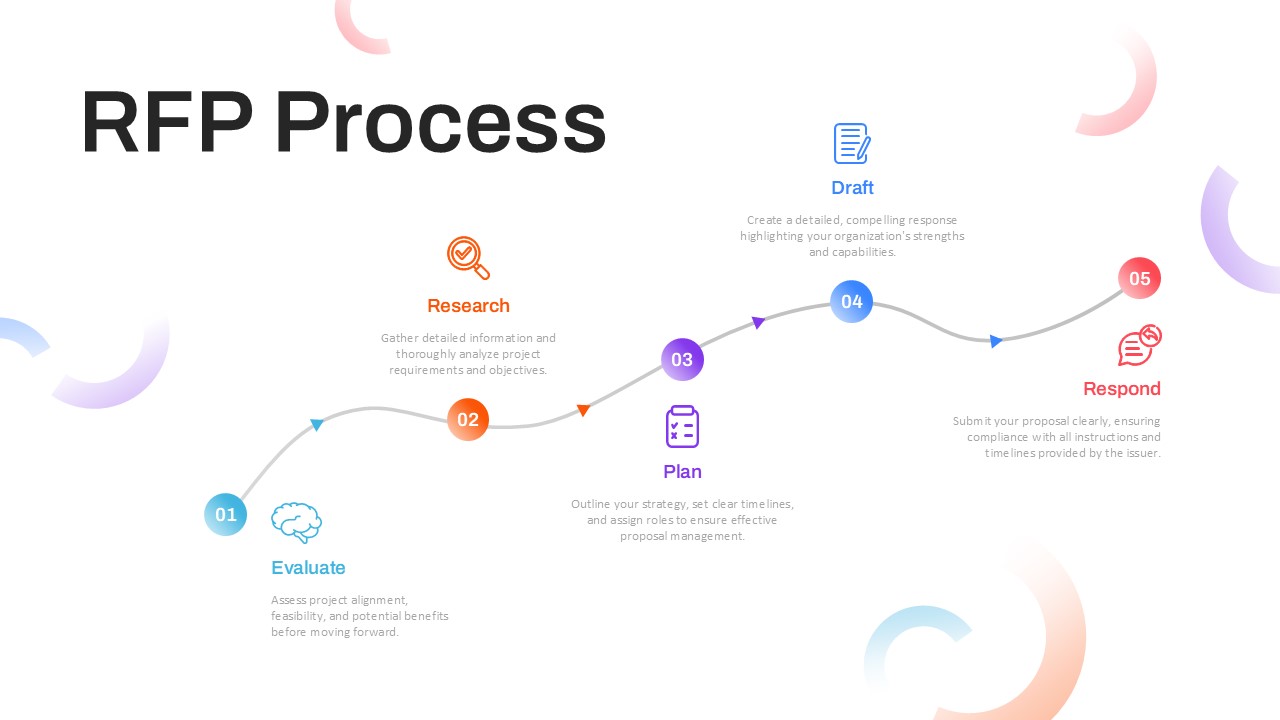
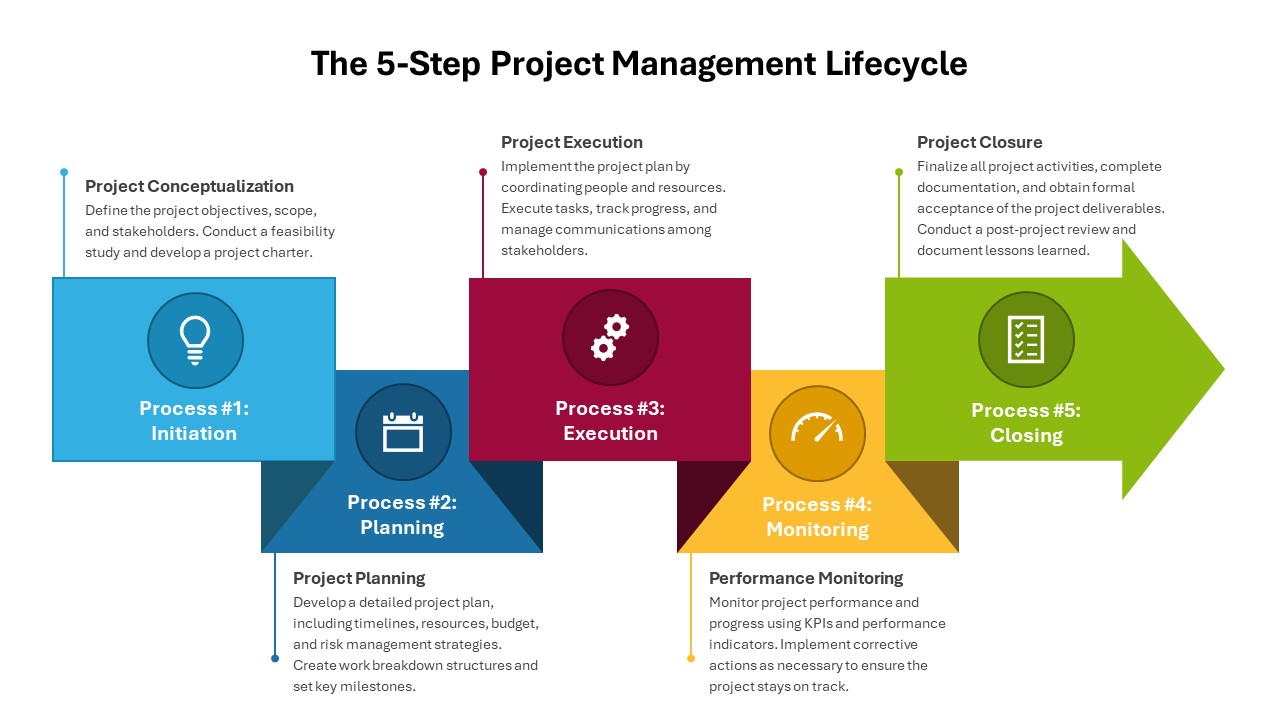
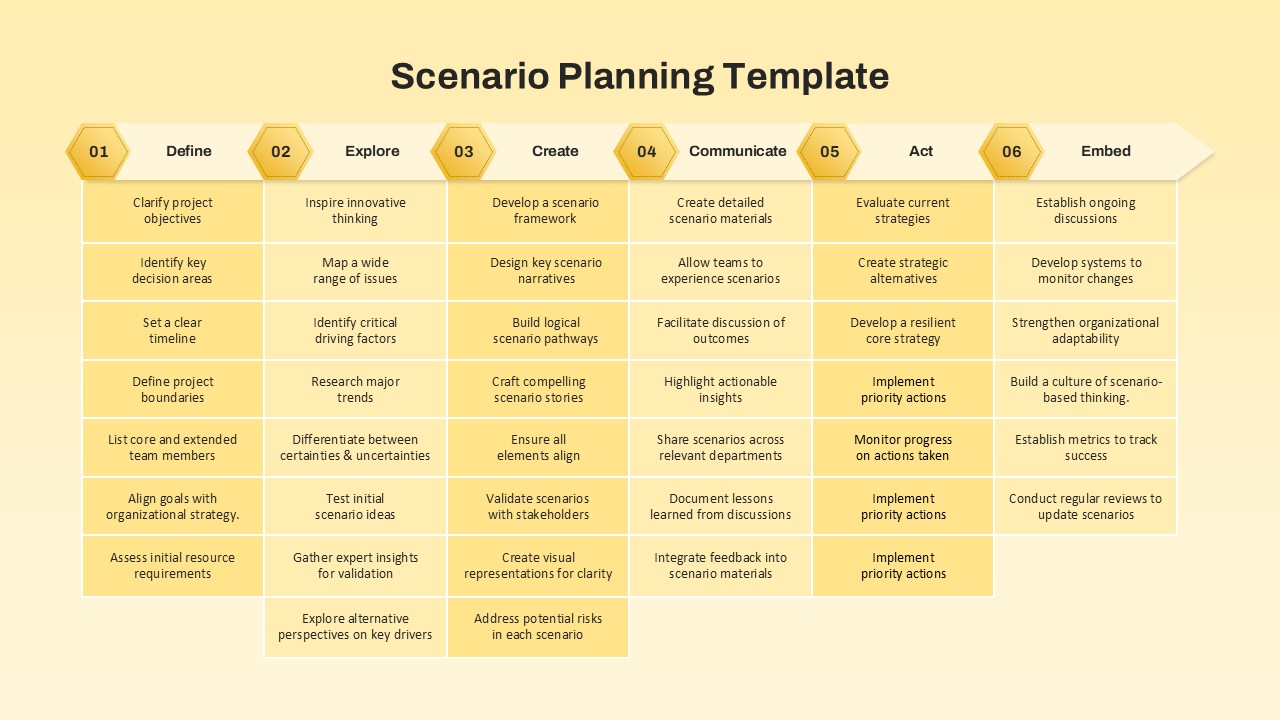
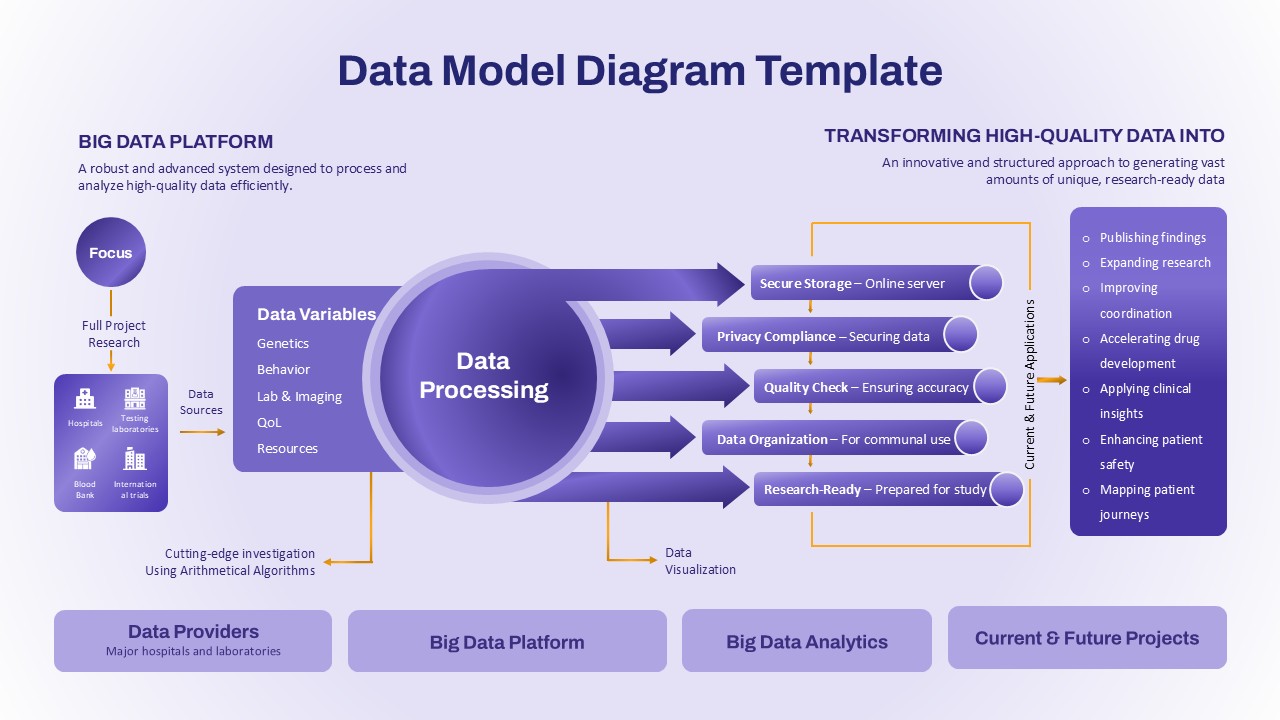
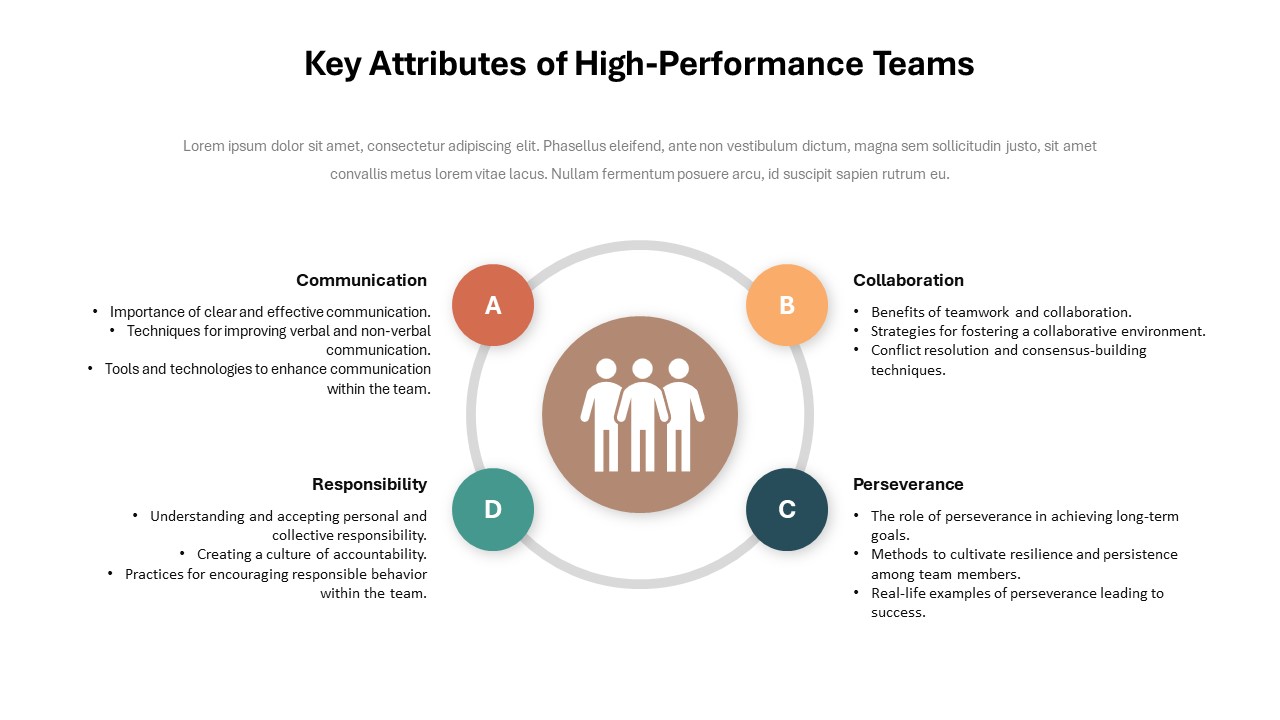
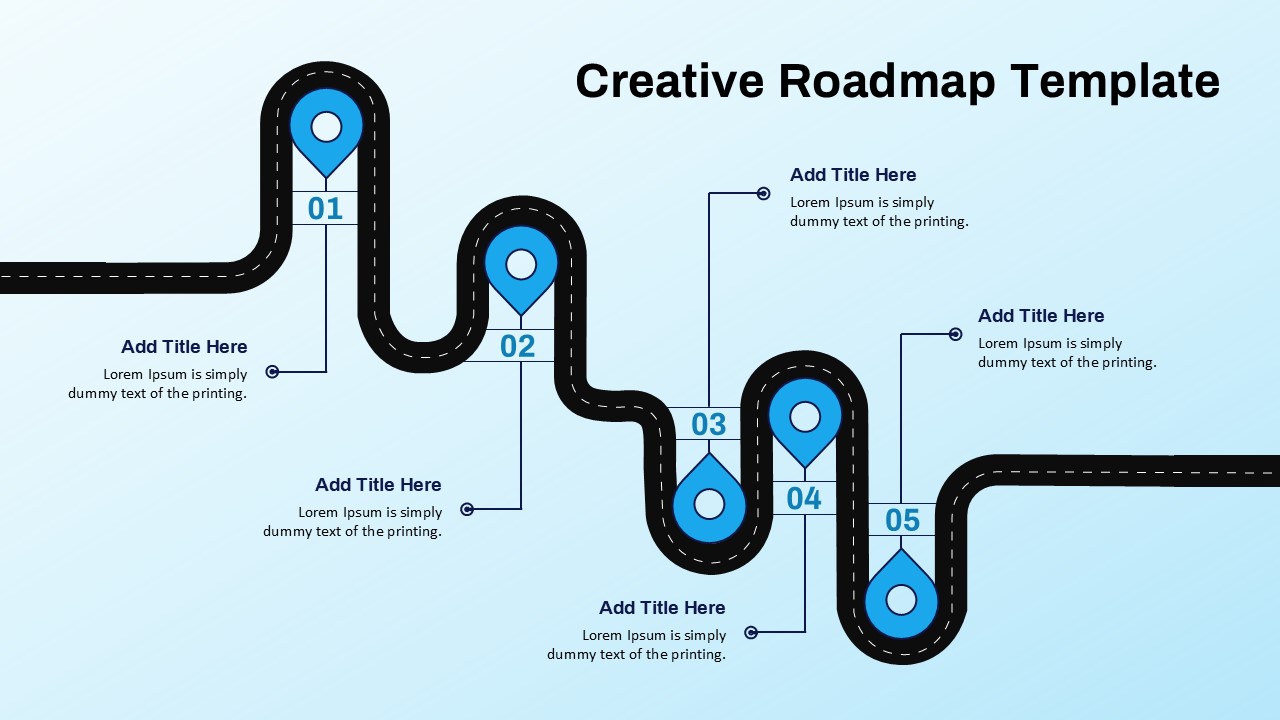
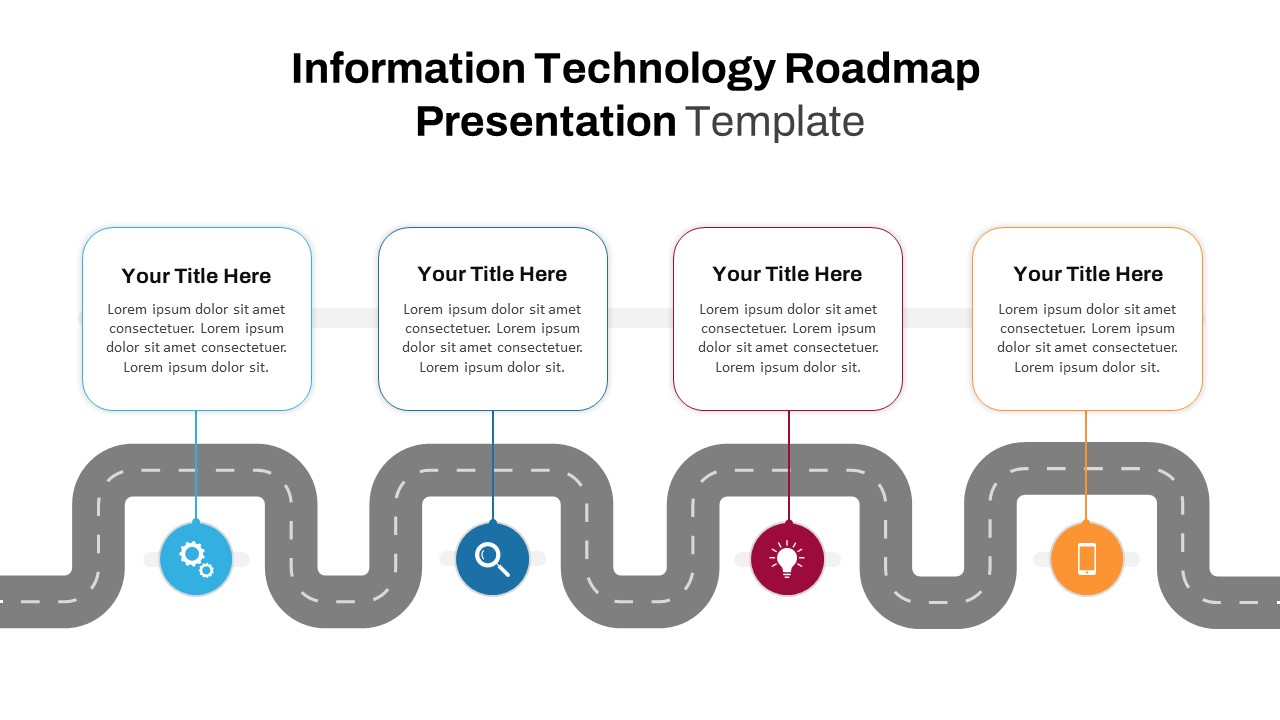
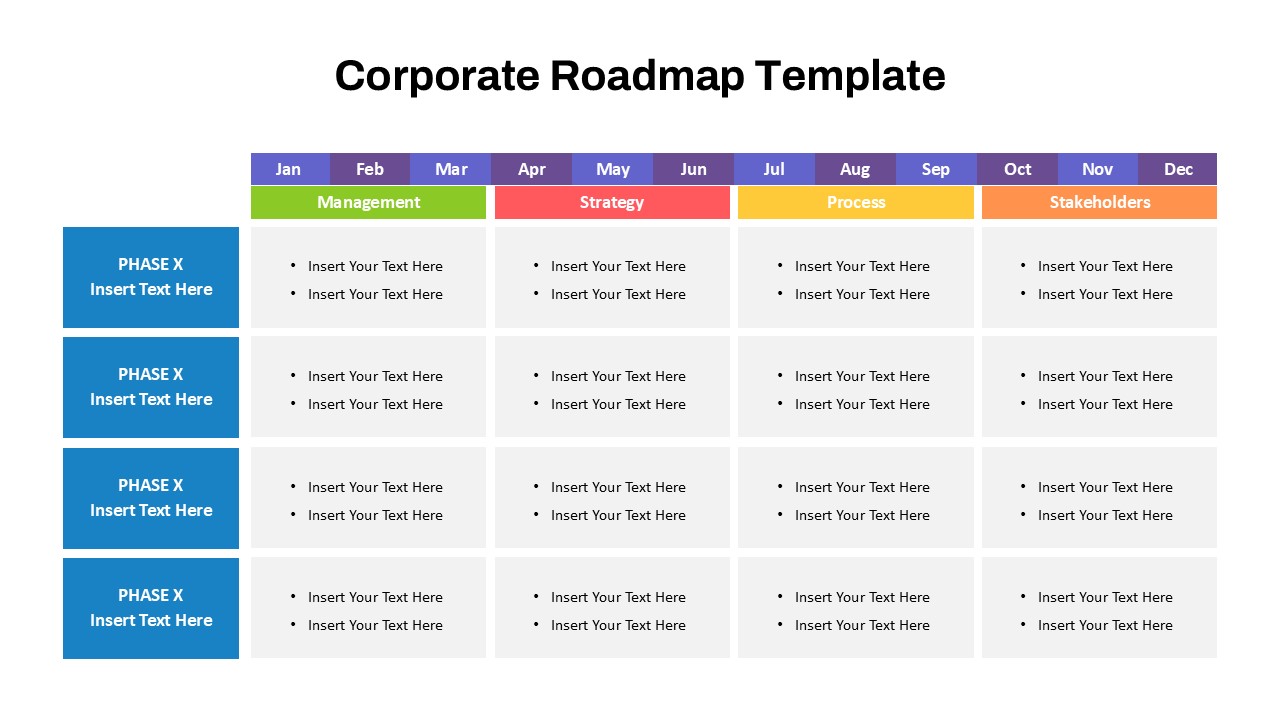
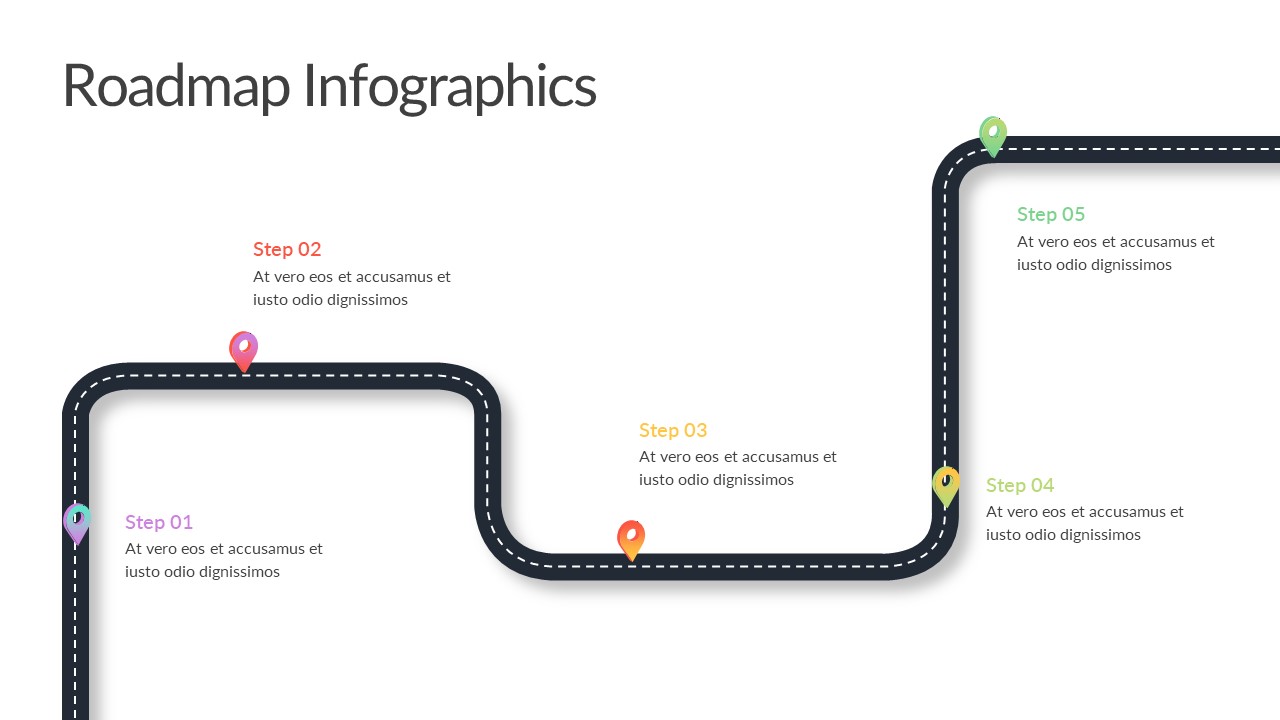
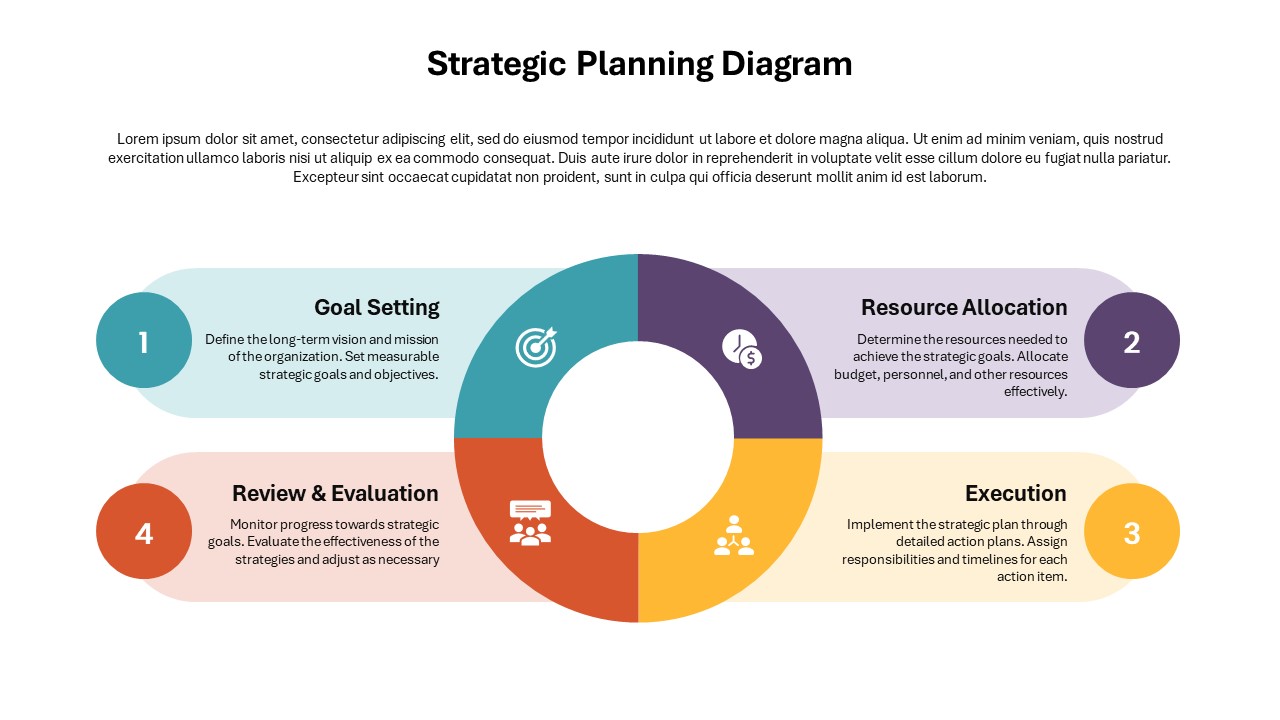
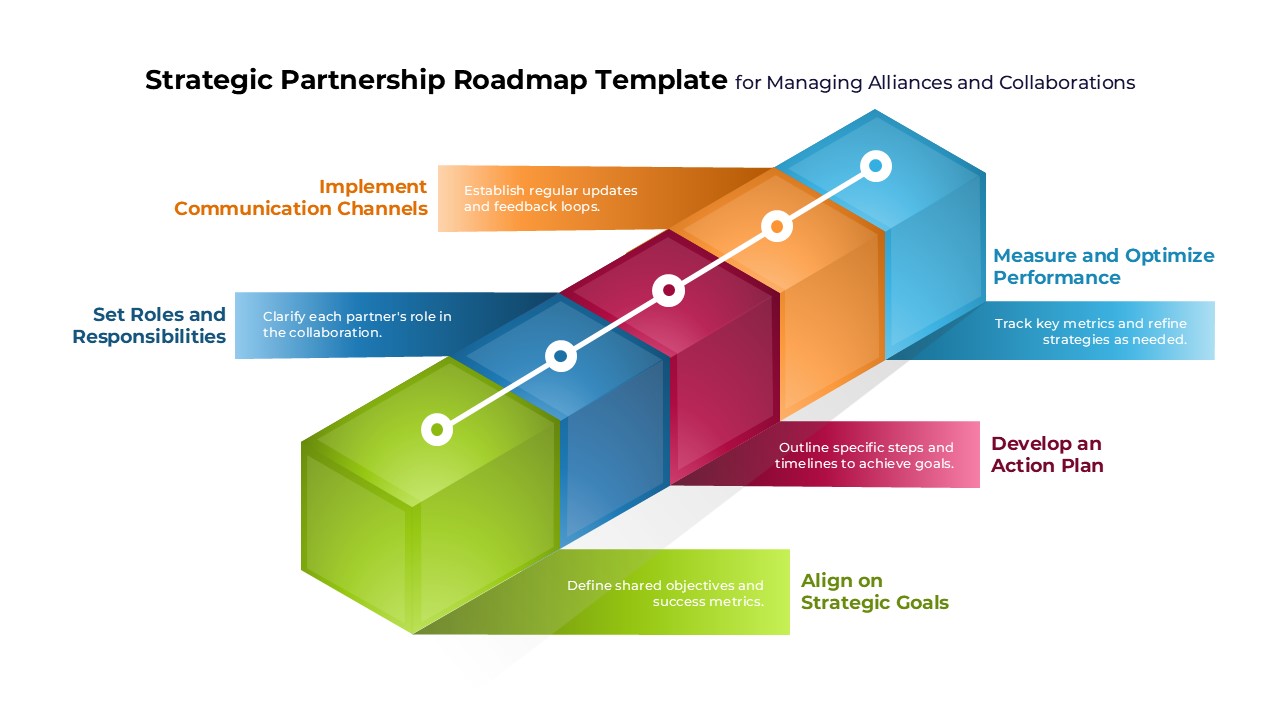
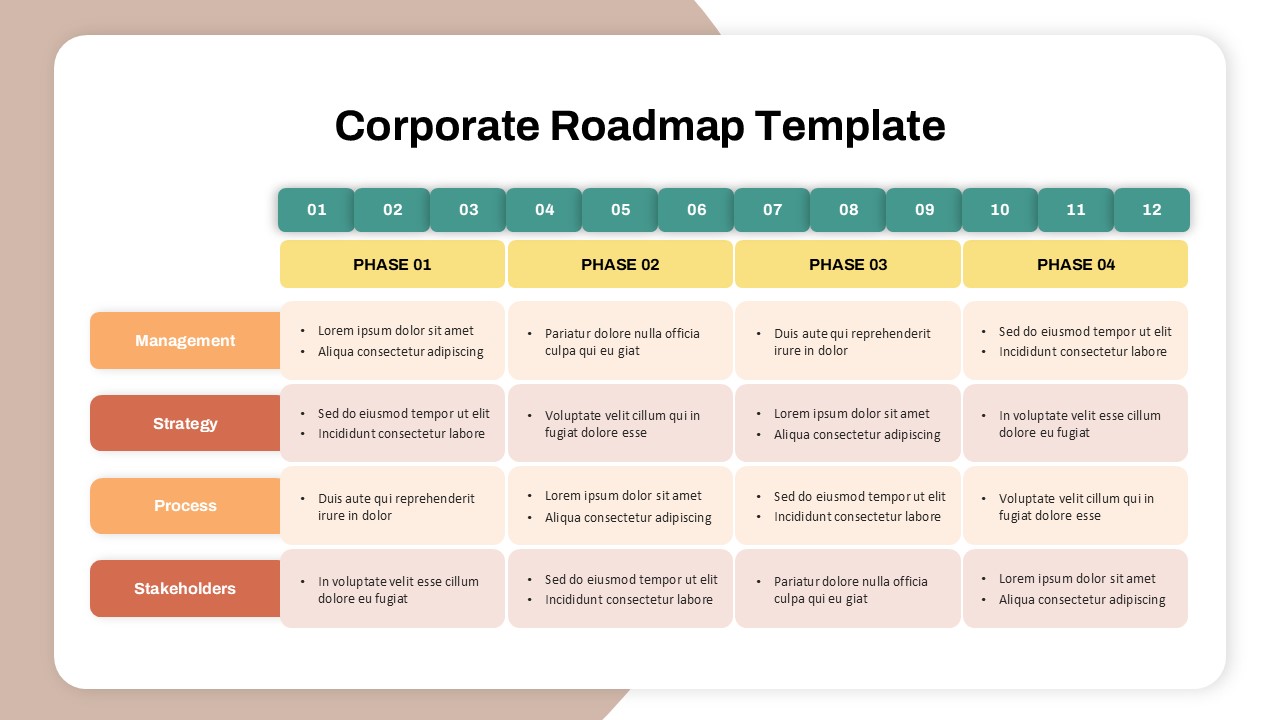
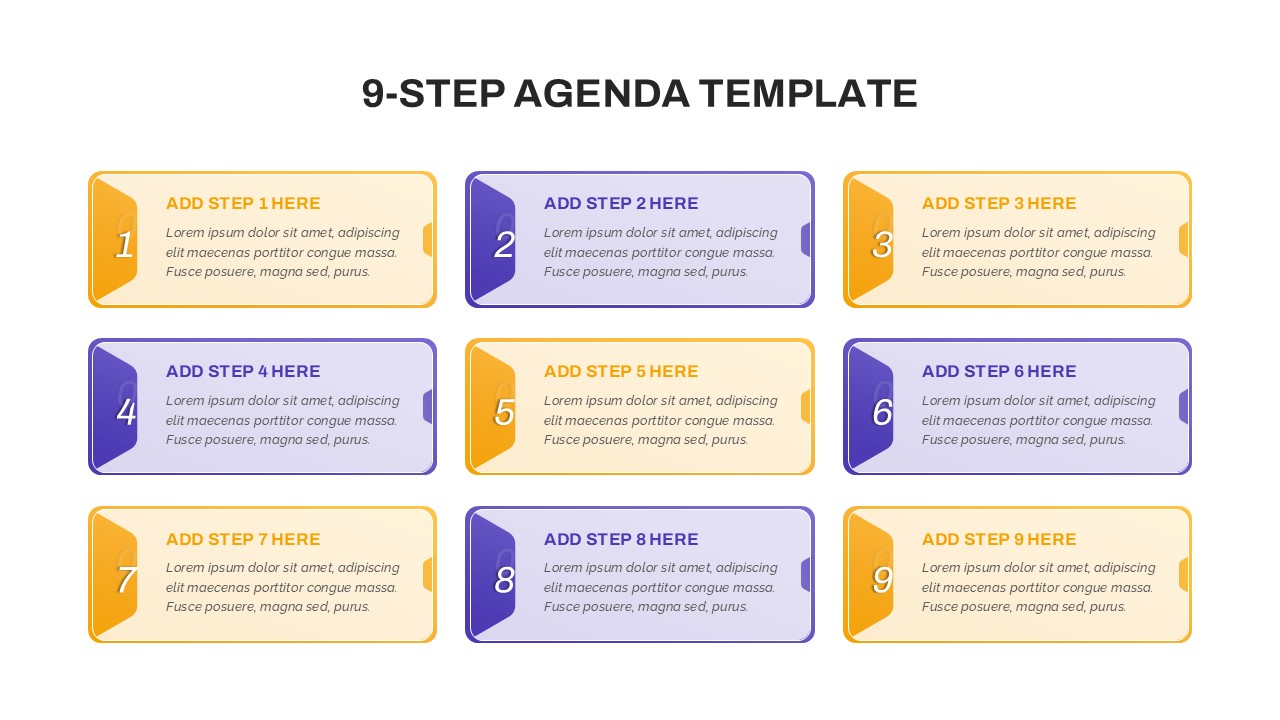
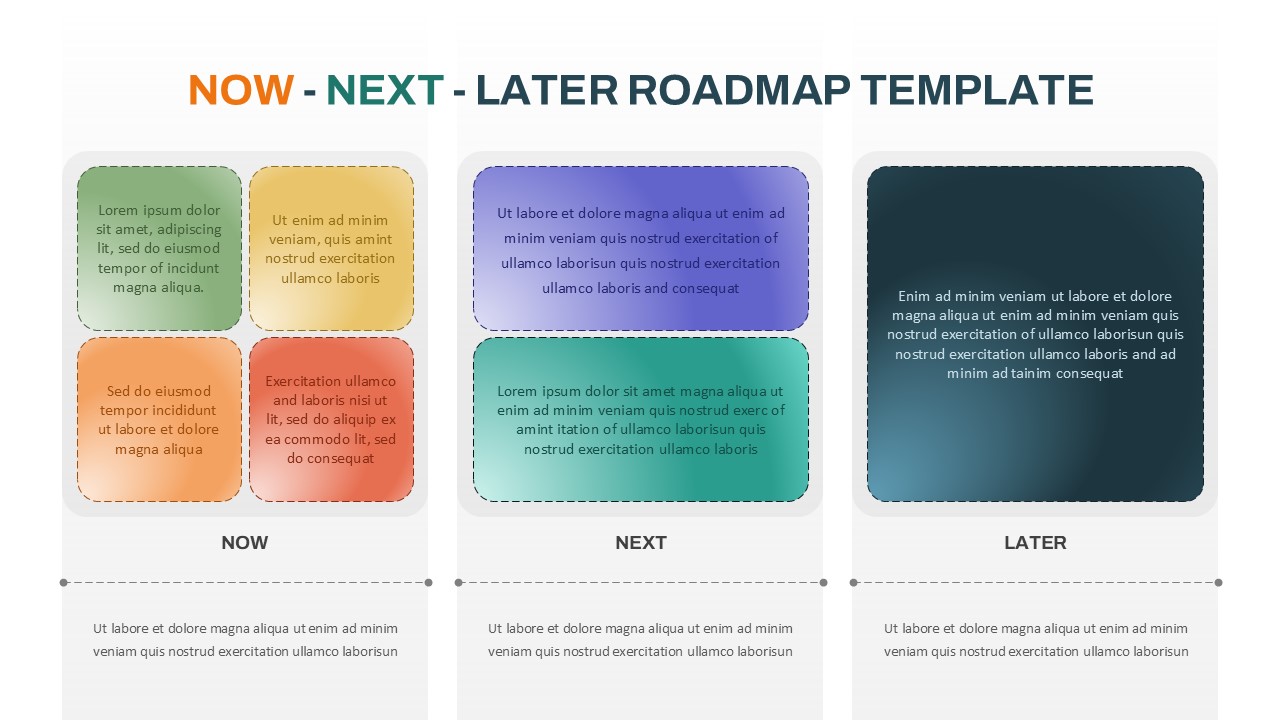
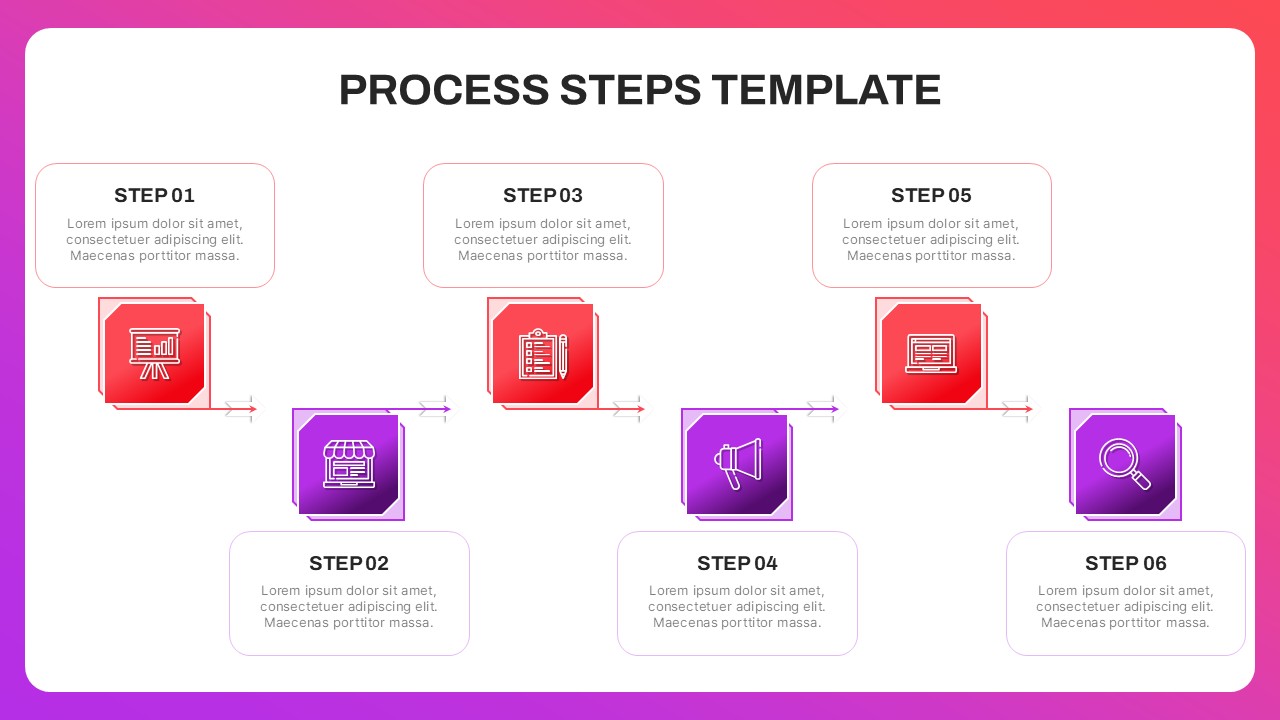
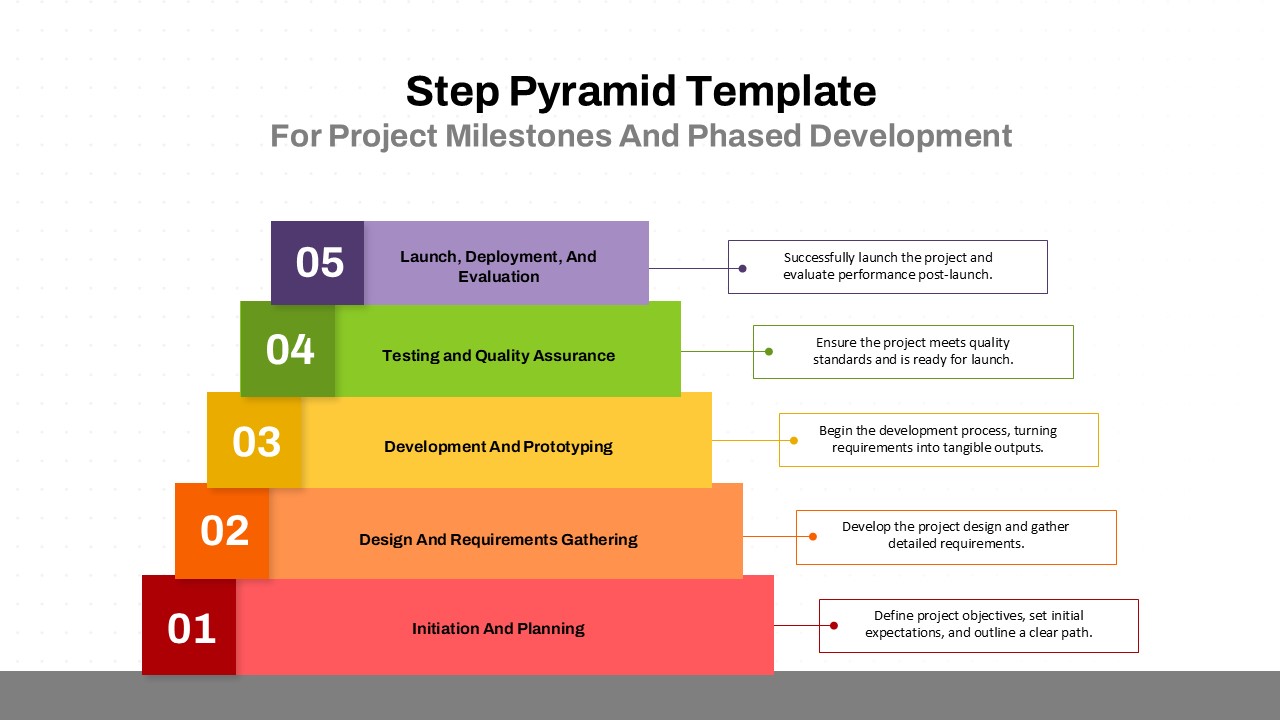
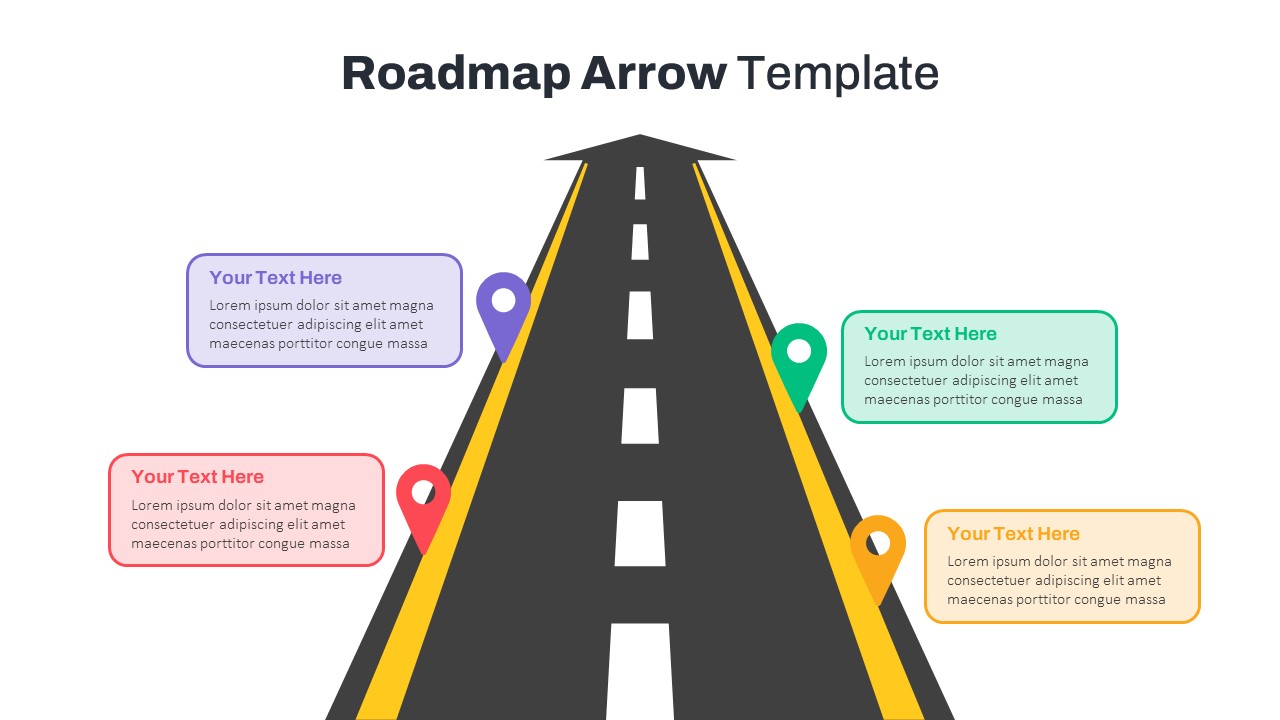
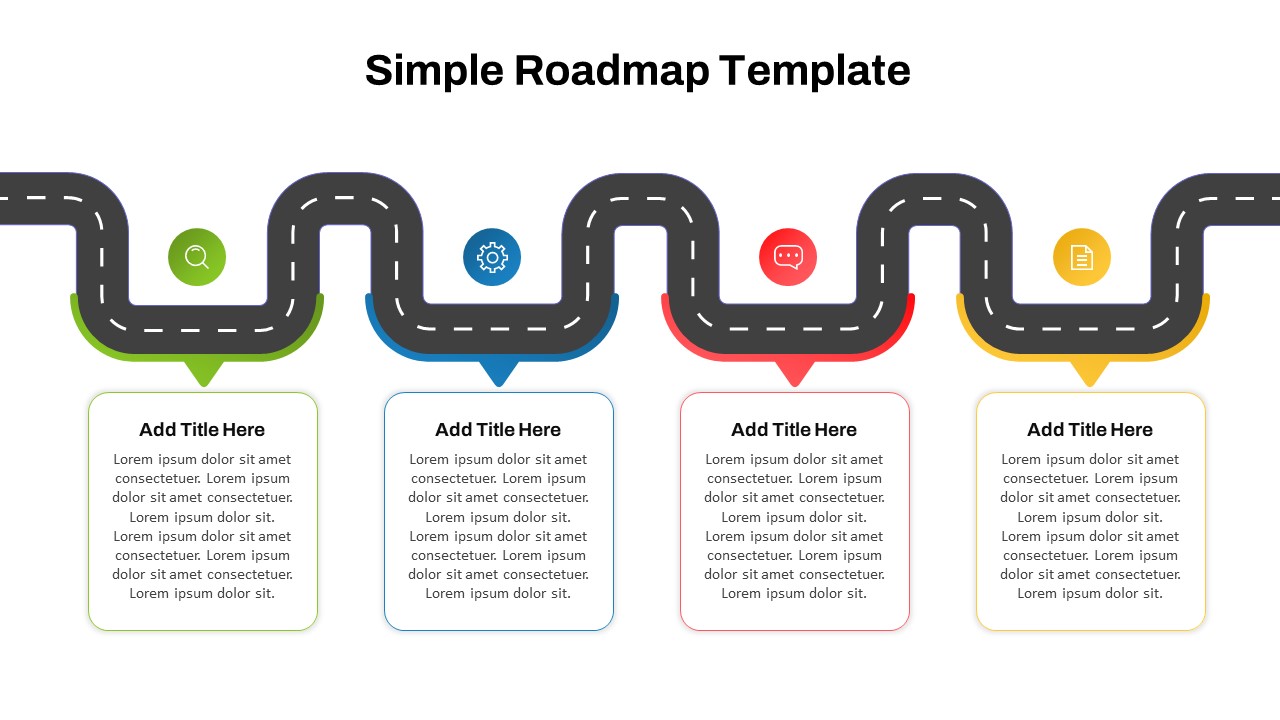
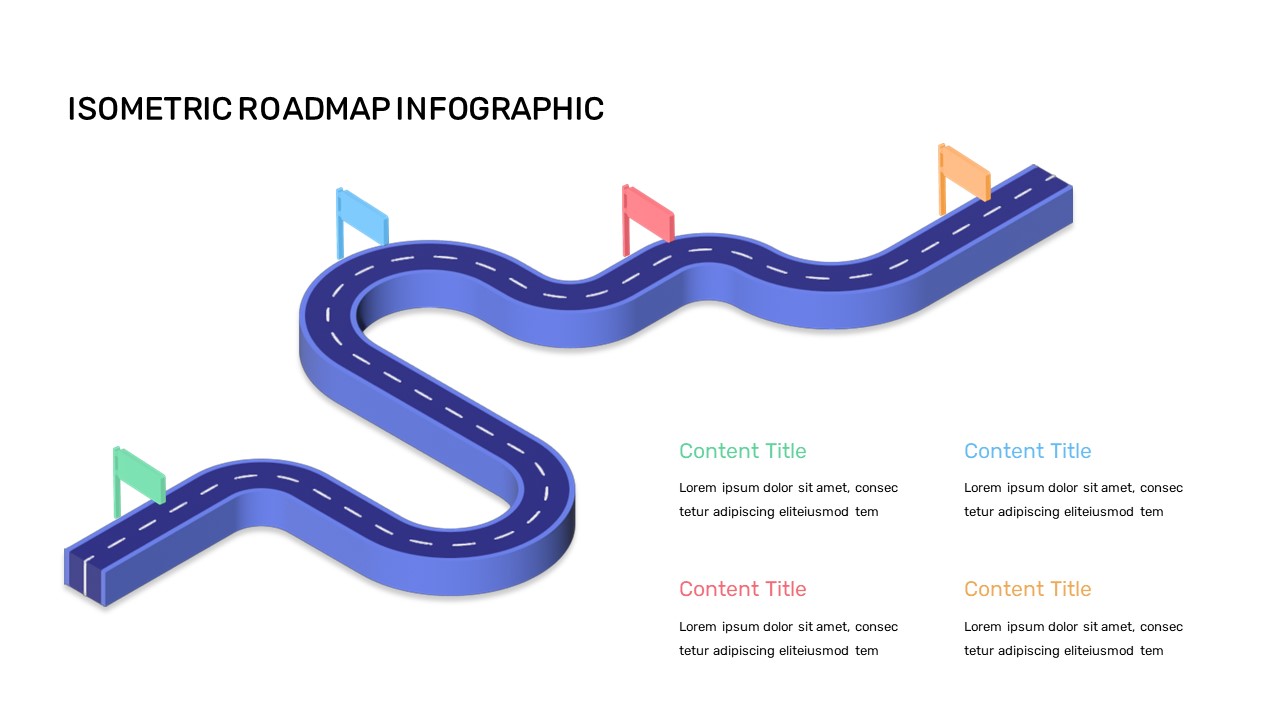
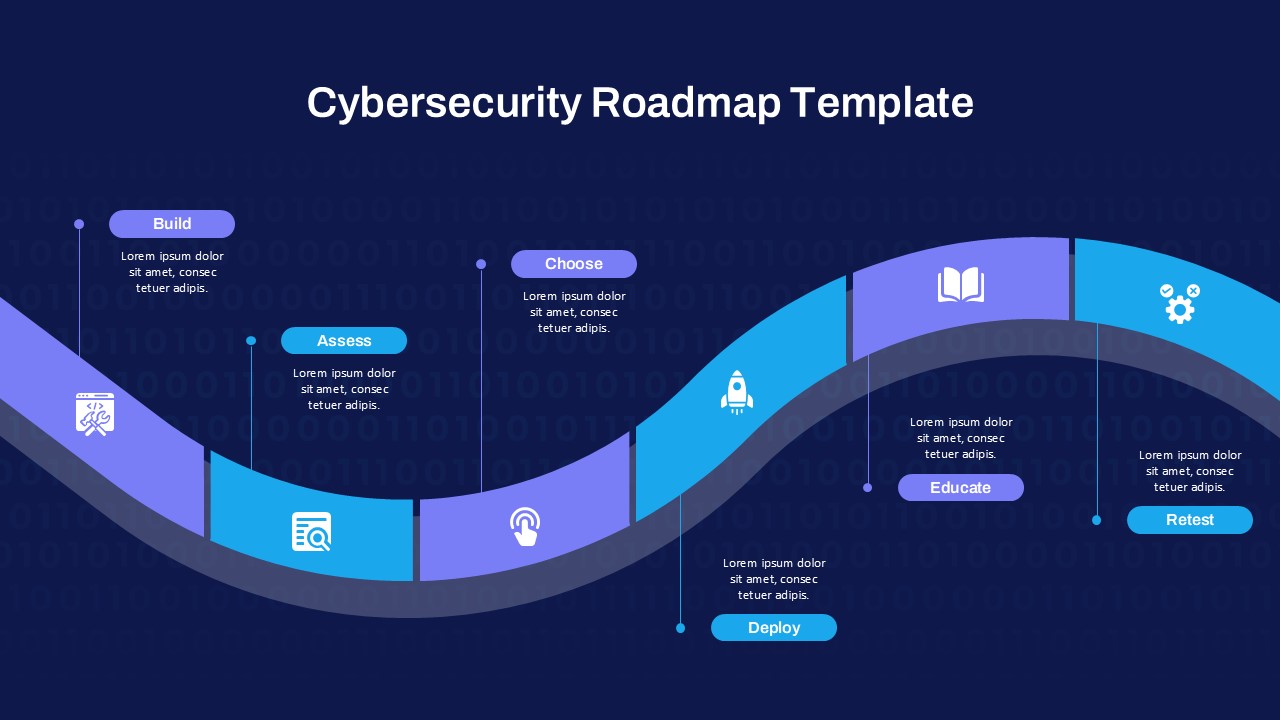
The design follows a smooth, wave-like pathway with six sequential stages: Build, Assess, Choose, Deploy, Educate, and Retest. Each step is color-coded and paired with relevant icons to enhance readability and support intuitive planning. This flow mirrors the real-world cybersecurity lifecycle—from establishing infrastructure and evaluating vulnerabilities to selecting tools, launching solutions, educating users, and conducting reassessments.
This roadmap is ideal for illustrating comprehensive security strategies in board meetings, risk management sessions, IT audits, or training workshops. Whether you’re deploying new protocols or updating an existing policy, this template ensures that stakeholders understand both the process and priorities involved in cybersecurity planning.
Fully customizable in PowerPoint and Google Slides, this template supports editing of each phase title, description, and color scheme. It enables tech teams to tailor the roadmap to specific security initiatives—such as network defense, endpoint protection, or data compliance—making it a powerful communication tool for both technical and non-technical audiences.
See more
Features of this template
Other User Cases of the Template:
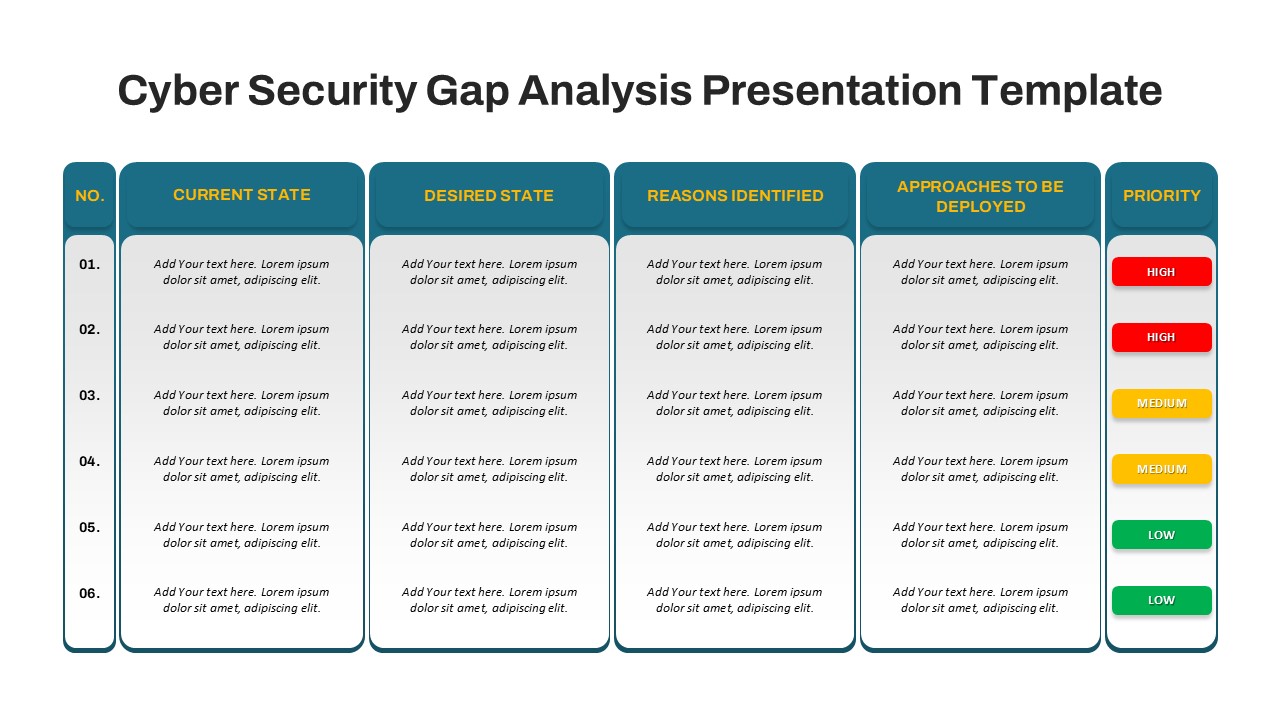
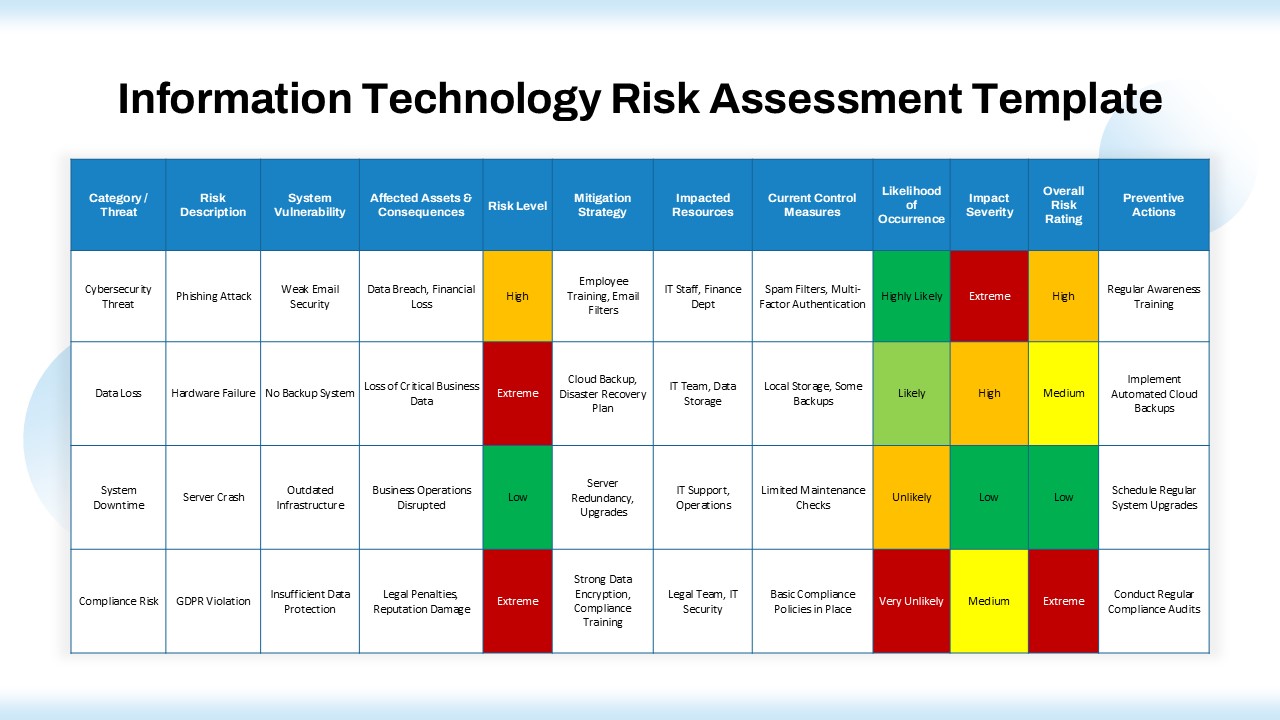
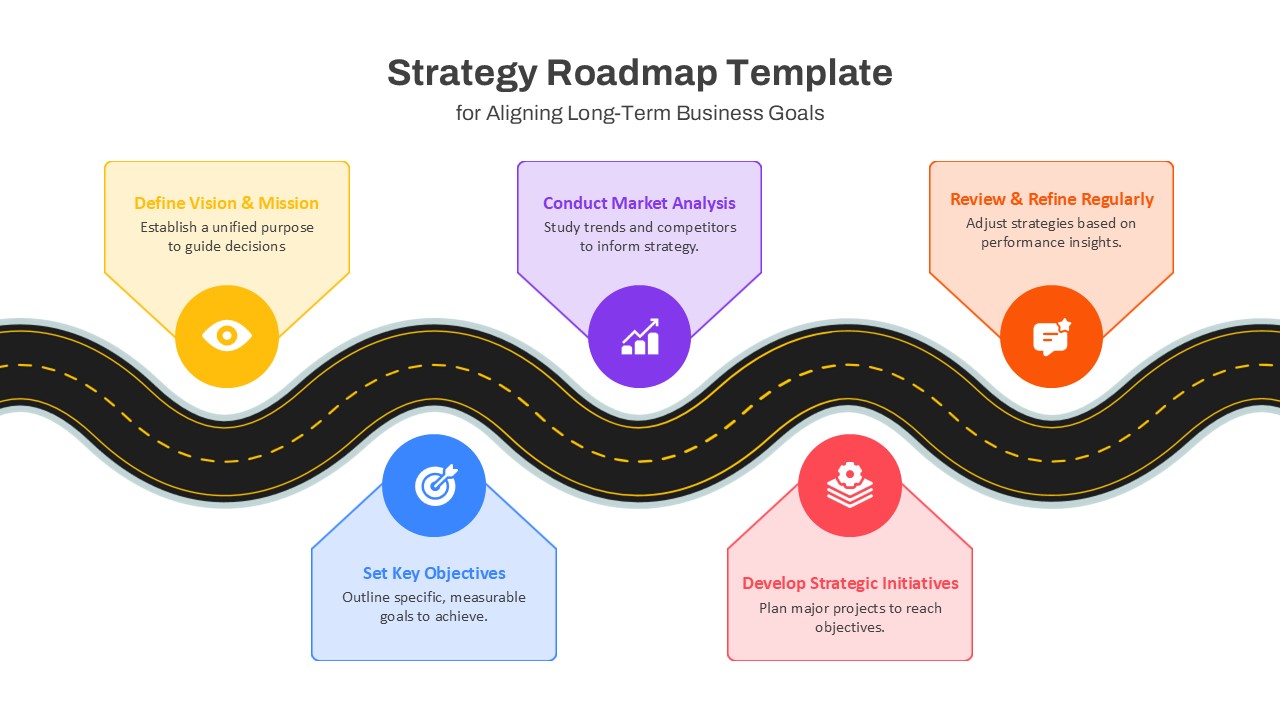
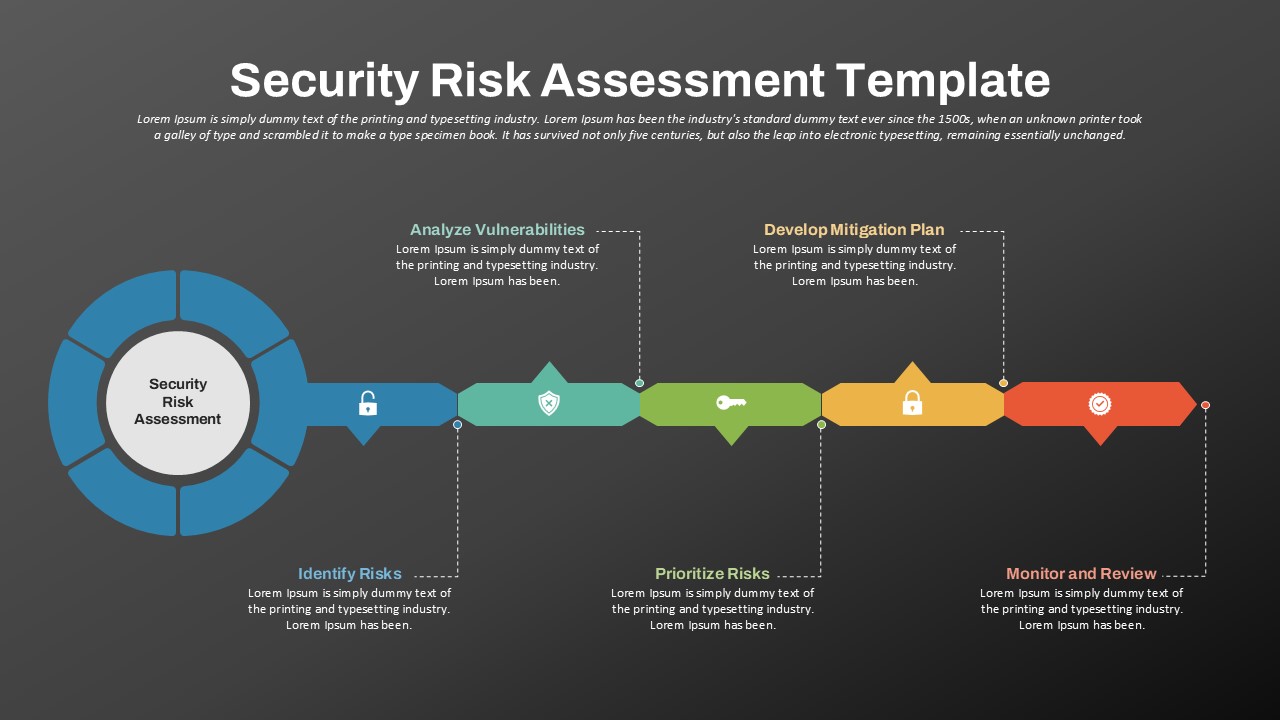
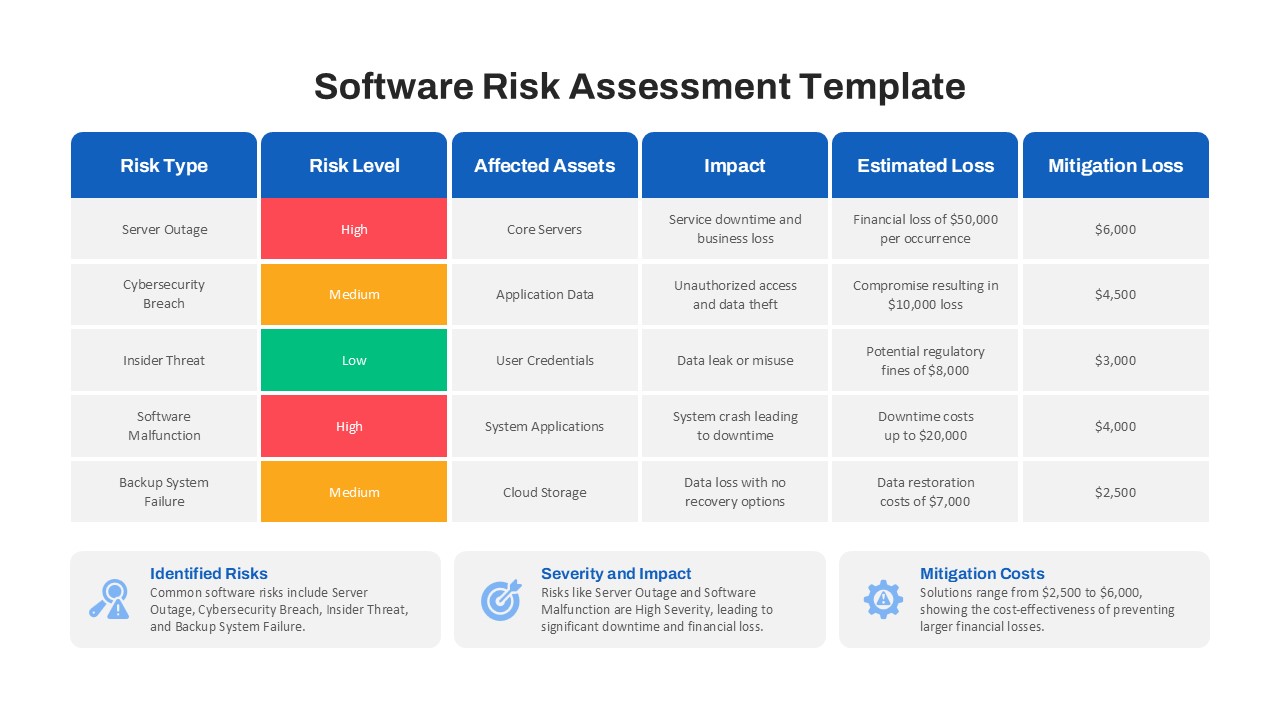
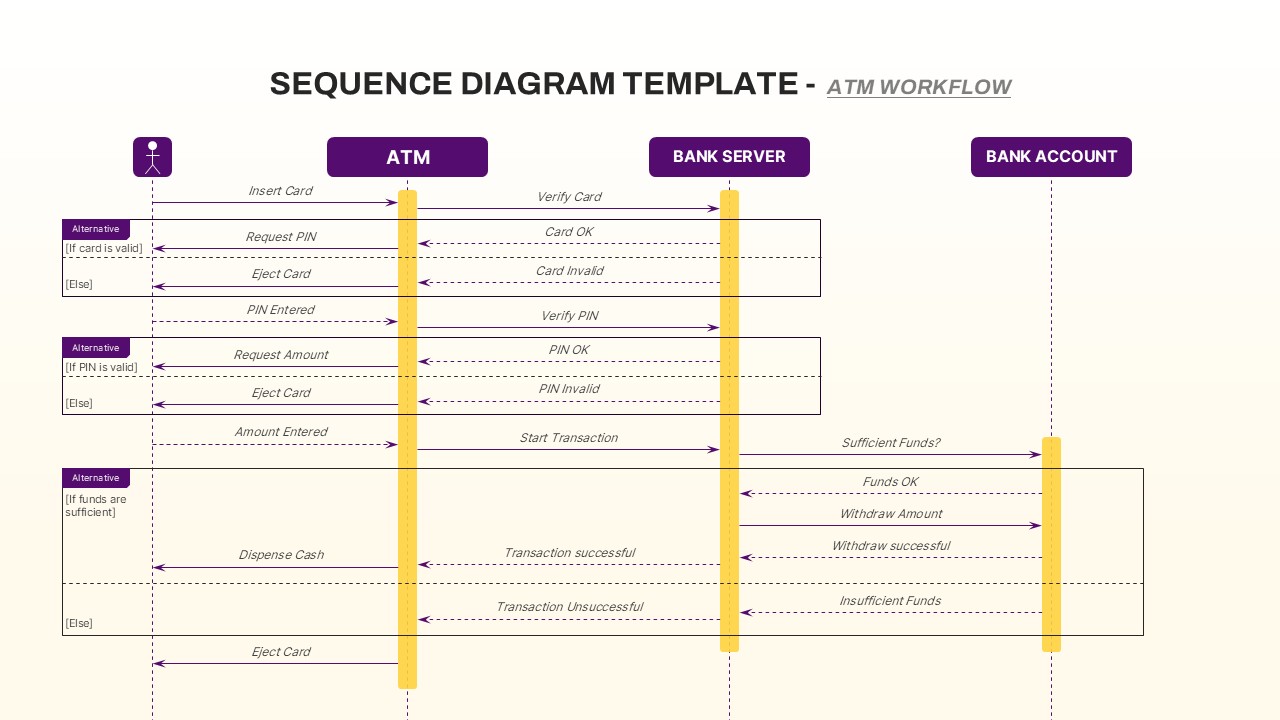
IT security strategy planning, cybersecurity awareness programs, risk assessment presentations, compliance project planning, network protection roadmaps, data privacy implementation, infosec maturity models, SOC team briefings, cloud security rollouts, vulnerability management tracking